





Trusted by
& many more
Trusted by
& many more
CurrentWare’s Security Solutions for CMMC Compliance
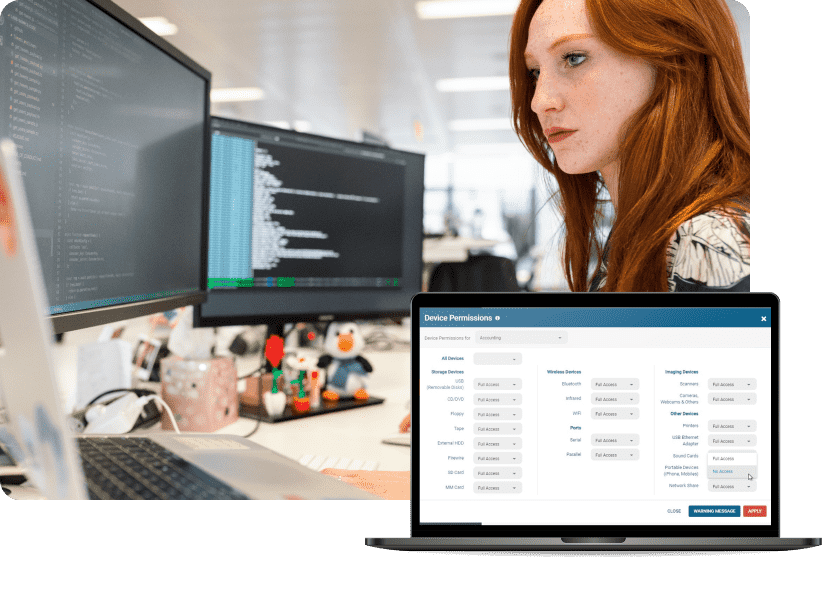
Control the Use of Removable Media On System Components
- Ensure only approved portable storage devices can be used on systems that interface with FCI & CUI
- Disable wireless connections through Bluetooth devices, infrared, and WiFi
- Block employees from using mobile devices, printers, and cameras to steal sensitive data
Related CMMC & NIST 800-171 Controls
CMMC MP.L2-3.8.7 Removable Media
CMMC AC.L2-3.1.18 Mobile Device Connection
CMMC CM.L2-3.4.6 Least Functionality
CMMC CM.L2-3.4.7 Nonessential Functionality
NIST SP 800-171 Rev 2 3.1.18
NIST SP 800-171 Rev 2 3.4.6 – 3.4.7
NIST SP 800-171 Rev 2 3.8.7
Detect and Prevent High-Risk Data Transfers
- Receive real time email alerts when employees violate your data security policies
- Track the data flow of CUI for non-compliant behavior that needs to be addressed
- Block file downloads/uploads based on file type to limit vectors for data egress
Related Controls
CMMC AC.L2-3.1.3 Control CUI Flow
CMMC AC.L1-3.1.2 Transaction & Function Control
CMMC AU.L2-3.3.1 System Auditing
CMMC AU.L2-3.3.2 User Accountability
CMMC AU.L2-3.3.6 Reduction & Reporting
CMMC CM.L2-3.4.6 Least Functionality
NIST SP 800-171 Rev 2 3.1.2 – 3.1.3
NIST SP 800-171 Rev 2 3.3.1 – 3.3.2
NIST SP 800-171 Rev 2 3.3.6
NIST SP 800-171 Rev 2 3.4.6
FAR Clause 52.204-21 b.1.ii
Monitor & Restrict the Resources Employees Access
- Control access to websites, applications, TCP/UDP ports, and intranet portals to enforce the principle of least privilege
- Apply deny-by-exception (blacklisting) policies to prevent the use of unauthorized software
- Control and monitor user-installed software to detect shadow IT and other high-risk programs
Related Controls
CMMC AC.L2-3.1.5 Least Privilege
CMMC AC.L1-3.1.20 External Connections
CMMC AC.L1-3.1.2 Transaction & Function Control
CMMC CM.L2-3.4.6 Least Functionality
CMMC CM.L2-3.4.7 Nonessential Functionality
CMMC CM.L2-3.4.8 Application Execution Policy
CMMC CM.L2-3.4.9 User-Installed Software
CMMC SC.L2-3.13.6 Network Communication by Exception
NIST SP 800-171 Rev 2 3.1.2
NIST SP 800-171 Rev 2 3.1.5
NIST SP 800-171 Rev 2 3.1.20
NIST SP 800-171 Rev 2 3.4.6-3.4.9
NIST SP 800-171 Rev 2 3.13.6
FAR Clause 52.204-21 b.1.ii-iii
Retain Logs of User Activity
- Monitor privileged accounts to ensure they are not being used to access nonsecurity functions
- Track web browsing, application usage, and file transfers to detect high-risk behavior
- Create and retain audit logs to enable the monitoring, analysis, investigation, and reporting of unlawful or unauthorized system activity
Related Controls
CMMC AC.L2-3.1.6 Non-Privileged Account Use
CMMC AU.L2-3.3.1 System Auditing
CMMC AU.L2-3.3.2 User Accountability
CMMC AU.L2-3.3.6 Reduction & Reporting
CMMC CM.L2-3.4.9 User-Installed Software
NIST SP 800-171 Rev 2 3.1.6
NIST SP 800-171 Rev 2 3.3.1-3.3.2
NIST SP 800-171 Rev 2 3.3.6
NIST SP 800-171 Rev 2 3.4.9
CMMC Compliance Requirements You Can Address With CurrentWare
| Controls | CurrentWare Modules & Features |
|---|---|
| AC.L2-3.1.3 Control CUI Flow – Control the flow of CUI in accordance with approved authorizations. NIST SP 800-171 Rev 2 3.1.3 | AccessPatrol | Data Loss Prevention
BrowseControl | Web Filter
|
| AC.L2-3.1.5 Least Privilege – Employ the principle of least privilege, including for specific security functions and privileged accounts. NIST SP 800-171 Rev 2 3.1.5 | AccessPatrol | Data Loss Prevention
BrowseControl | Web Filter
|
| AC.L2-3.1.6 Non-Privileged Account Use – Use non-privileged accounts or roles when accessing nonsecurity functions. NIST SP 800-171 Rev 2 3.1.6 | BrowseReporter | User Activity Monitoring
|
| AC.L2-3.1.9 Privacy & Security Notices – Provide privacy and security notices consistent with applicable CUI rules. NIST SP 800-171 Rev 2 3.1.9 | AccessPatrol | Data Loss Prevention
|
| AC.L2-3.1.18 Mobile Device Connection – Control connection of mobile devices. NIST SP 800-171 Rev 2 3.1.18 | AccessPatrol | Data Loss Prevention
|
| AC.L1-3.1.2 Transaction & Function Control – Limit information system access to the types of transactions and functions that authorized users are permitted to execute. FAR Clause 52.204-21 b.1.ii NIST SP 800-171 Rev 2 3.1.2 | BrowseControl | Web Filter
|
| AC.L1-3.1.20 External Connections – Verify and control/limit connections to and use of external information systems. FAR Clause 52.204-21 b.1.iii NIST SP 800-171 Rev 2 3.1.20 | BrowseControl | Web Filter
|
| Controls | CurrentWare Modules & Features |
|---|---|
| AU.L2-3.3.1 System Auditing – Create and retain system audit logs and records to the extent needed to enable the monitoring, analysis, investigation, and reporting of unlawful or unauthorized system activity. NIST SP 800-171 Rev 2 3.3.1 | AccessPatrol | Data Loss Prevention
BrowseReporter | User Activity Monitoring
enPowerManager | Remote PC Power Manager
|
| AU.L2-3.3.2 User Accountability – Ensure that the actions of individual system users can be uniquely traced to those users, so they can be held accountable for their actions. NIST SP 800-171 Rev 2 3.3.2 | All CurrentWare modules distinguish between specific user accounts, ensuring that all user activity is attributable to specific users |
| AU.L2-3.3.5 Audit Correlation – Correlate audit record review, analysis, and reporting processes for investigation and response to indications of unlawful, unauthorized, suspicious, or unusual activity. NIST SP 800-171 Rev 2 3.3.5 | AccessPatrol | Data Loss Prevention
BrowseReporter | User Activity Monitoring
enPowerManager | Remote PC Power Manager
|
| AU.L2-3.3.6 Reduction & Reporting – Provide audit record reduction and report generation to support on-demand analysis and reporting. NIST SP 800-171 Rev 2 3.3.6 | User activity data collected by CurrentWare can be exported as PDF or CSV reports |
| AU.L2-3.3.9 Audit Management – Limit management of audit logging functionality to a subset of privileged users. NIST SP 800-171 Rev 2 3.3.9 | With CurrentWare’s operator accounts you can ensure access to user activity data is protected behind unique admin accounts with two-factor authentication capabilities |
| Controls | CurrentWare Modules & Features |
|---|---|
| CM.L2-3.4.1 System Baselining – Establish and maintain baseline configurations and inventories of organizational systems (including hardware, software, firmware, and documentation) throughout the respective system development life cycles. NIST SP 800-171 Rev 2 3.4.1 | BrowseReporter | User Activity Monitoring
|
| CM.L2-3.4.6 Least Functionality – Employ the principle of least functionality by configuring organizational systems to provide only essential capabilities. NIST SP 800-171 Rev 2 3.4.6 | AccessPatrol | Data Loss Prevention
BrowseControl | Web Filter
|
| CM.L2-3.4.7 Nonessential Functionality – Restrict, disable, or prevent the use of nonessential programs, functions, ports, protocols, and services. NIST SP 800-171 Rev 2 3.4.7 | AccessPatrol | Data Loss Prevention
BrowseControl | Web Filter
|
| CM.L2-3.4.8 Application Execution Policy – Apply deny-by-exception (blacklisting) policy to prevent the use of unauthorized software or deny-all, permit-by-exception (whitelisting) policy to allow the execution of authorized software. NIST SP 800-171 Rev 2 3.4.8 | BrowseControl | Web Filter
|
| CM.L2-3.4.9 User-Installed Software – Control and monitor user-installed software. NIST SP 800-171 Rev 2 3.4.9 | AccessPatrol | Data Loss Prevention
BrowseControl | Web Filter
BrowseReporter | User Activity Monitoring
|
| Controls | CurrentWare Modules & Features |
|---|---|
| AT.L2-3.2.1 Role-Based Risk Awareness – Ensure that managers, systems administrators, and users of organizational systems are made aware of the security risks associated with their activities and of the applicable policies, standards, and procedures related to the security of those systems. NIST SP 800-171 Rev 2 3.2.1 | AccessPatrol | Data Loss Prevention
BrowseControl | Web Filter
|
| Controls | CurrentWare Modules & Features |
|---|---|
| MP.L2-3.8.7 Removable Media – Control the use of removable media on system components. NIST SP 800-171 Rev 2 3.8.7 | AccessPatrol | Data Loss Prevention
|
| MP.L2-3.8.8 Shared Media – Prohibit the use of portable storage devices when such devices have no identifiable owner. NIST SP 800-171 Rev 2 3.8.8 | AccessPatrol | Data Loss Prevention
|
| Controls | CurrentWare Modules & Features |
|---|---|
| SC.L2-3.13.6 Network Communication by Exception – Deny network communications traffic by default and allow network communications traffic by exception (i.e., deny all, permit by exception). NIST SP 800-171 Rev 2 3.13.6 | BrowseControl | Web Filter
|
| SC.L2-3.13.14 Voice over Internet Protocol – Control and monitor the use of Voice over Internet Protocol (VoIP) technologies. NIST SP 800-171 Rev 2 3.13.14 | BrowseControl | Web Filter
BrowseReporter | User Activity Monitoring
|
CASE STUDY
Boston Centerless Scales Production & Secures Their Remote Workforce
CurrentWare has been nothing but supportive of us since we started. This is probably one of the best systems that we’ve ever invested in.
Once we got CurrentWare installed it opened the door for remote work for us; we could control the equipment and make sure our people were being productive and safe.
See What Our Customers Have to Say
This software helps us to achieve compliance with industry and government requirements with respect to controlling the use of removable storage media. It fits the bill perfectly.
Matthew W, Project Manager
Aviation & Aerospace Industry, 11-50 employees
In my nearly 40 years in the IT business I’ve worked with a lot of support teams. I really appreciate CurrentWare going the extra mile to help me get the most out of the product. They’ve definitely outweighed any of the other competitors that I’ve looked at.
J.S, Managed Services Provider
Vehicle Dealership, 150-200 Employees
The reports are very easy to understand and the fact that they can be emailed to you on a schedule is amazing... Customer support has been fantastic every time I've had to reach out to them; I highly recommend them!
Kristen S, Associate IT Director
The Coding Network, 700+ Employees
We have experienced data leaks by dishonest employees in the past and AccessPatrol has helped us avoid them and work with greater security and peace of mind for us and our customers.
Julio V, Head of Information Technology
Financial Services Industry, 10,001+ employees
FREE DOWNLOAD
Removable Media Policy Template
Download this data security policy template to prevent data leakage to USB flash drives and other removable storage devices.
- Set data security standards for portable storage
- Define the acceptable use of removable media
- Inform your users about their security responsibilities
CurrentWare's Key Features
User Activity Monitoring
Track web browsing, software use, search queries, and more
Screenshot Monitoring
Take automatic screenshots or remotely view desktops
Track Software Usage
Get insights into software usage trends in your organization
Transparent & Stealth Modes
Run silently in the background or provide notice of monitoring
Block USB & Other Devices
Set full access, read only or no access on storage devices
Device Whitelist
Allow only authorized storage devices to be used
Block File Transfers
Prevent files from being transferred to portable storage
DLP Activity Reports
Track file transfers, storage device use, file operations, and more
Block Websites
Block websites based on
URLs & content categories
Block Downloads/Uploads
Prevent uploading and downloading based on file type
Application Blacklisting
Block specific Windows
applications from launching
PC Power Management
Remotely track and control PC power states
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server
Learn How to Meet These Compliance Requirements With CurrentWare
NERC CIP
Protect TCAs & BCSI From Insider Threats
ISO 27001
Increase the Maturity of Your ISO27K ISMS
NIST 800-171/53
Protect Controlled Unclassified Information
CIPA for Education
Qualify for the FCC’s
E-Rate Program
Cyber Essentials
Critical Security Controls For Your Assessment
CMMC
Protect CUI to qualify for DoD contracts
Frequently Asked Questions
What is CMMC compliance software?
CMMC compliance software helps U.S. Department of Defense (DoD) contractors meet cybersecurity requirements by enforcing access control policies, logging user activity, and securing Controlled Unclassified Information (CUI).
CurrentWare supports CMMC Level 1 and Level 2 compliance by providing endpoint monitoring, USB control, internet restriction, and audit-ready reporting tools essential for meeting cybersecurity practices derived from NIST SP 800‑171.
What are the CMMC requirements?
The Cybersecurity Maturity Model Certification (CMMC) includes practices across 17 domains, such as Access Control (AC), Audit and Accountability (AU), and Media Protection (MP).
For Level 2 compliance, organizations must implement controls such as
- Role-based access and least privilege enforcement
- Endpoint activity logging
- Media and removable device control
- Incident detection and response capabilities
CurrentWare enforces these controls through solutions like
- AccessPatrol – USB device control
- BrowseReporter – User activity logging
- BrowseControl – Internet and app restrictions
How does activity monitoring support CMMC compliance?
Activity monitoring supports multiple Level 2 CMMC practices, including:
- AU.L2-3.3.1 (Create and retain audit logs)
- AU.L2-3.3.2 (Protect audit log integrity)
- IR.L2-3.6.1 (Establish incident handling capability)
CurrentWare’s BrowseReporter logs web activity, app usage, logon events, and idle time to provide a detailed audit trail for internal and external assessments, enhancing accountability and incident response readiness.
Why is USB device control important for CMMC?
CMMC requires strict control over removable media to prevent data leaks and unauthorized transfers, specifically under:
- MP.L2-3.8.7 – “Restrict the use of removable media…”
- MP.L2-3.8.8 – “Prohibit the use of portable storage devices when necessary.”
AccessPatrol, CurrentWare’s device control solution, allows administrators to block unauthorized USB devices, monitor file transfers, and apply granular access rules based on user, device type, or organizational policy.
Can CurrentWare help achieve CMMC Level 2?
Yes. CurrentWare provides tools that support key CMMC Level 2 technical controls, including:
- Access Control (AC): Enforce least privilege through device and internet restrictions
- Audit & Accountability (AU): Maintain audit-ready logs of user behavior
- Media Protection (MP): Control the use of USB and removable media
- Incident Response (IR): Enable detection and investigation of suspicious activity
This makes CurrentWare a practical solution for organizations preparing for Level 2 assessments.
How do I prepare for a CMMC audit?
To prepare for a CMMC audit:
- Enforce user and device policies across the IT environment
- Log all user activity (web, apps, logins, USB usage)
- Generate compliance reports that align with CMMC practices
CurrentWare equips organizations with the evidence needed to demonstrate compliance, helping streamline the third-party audit process and meet CMMC readiness milestones.
Does CMMC compliance apply to remote or hybrid teams?
Yes. CMMC compliance applies regardless of employee location.
CurrentWare enables secure compliance for hybrid and remote workforces by
- Remotely enforcing security policies (web filtering, USB blocking)
- Logging endpoint activity outside the corporate network
- Centrally managing compliance configurations across all devices
This ensures consistent application of CMMC controls across all work environments.
