Trusted by
& many more
Trusted by
& many more
Detect & Prevent Industrial Espionage
Concerned that disgruntled employees or contractors may attempt to steal data? Use CurrentWare’s data loss prevention solutions to protect sensitive customer data, trade secrets, and PII against insider threats.
- Monitor and restrict employee and contractor access to the internet and software
- Prevent the use of unauthorized USB storage devices and cloud storage services
- Maintain auditable records of how employees interact with devices that are used to handle sensitive data
Protect Sensitive Data
In an evolving threat landscape, manufacturers need to develop a strategy—and deploy the appropriate technology—to defend their operations.
- Monitor employee computer usage for high-risk file transfers, harmful web activities, and other suspicious activity.
- Meet data security requirements for government contracts, protect sensitive data against theft, and capture evidence of undesirable computer usage.
- Block unauthorized USB devices to mitigate data theft and the introduction of malicious software into manufacturing systems
Meet Compliance Requirements
Protect regulated data with CurrentWare’s robust data loss prevention, endpoint security, and user activity monitoring features.
Address critical cybersecurity requirements for frameworks like NIST 800-171, and DoD regulations such as CMMC, ITAR, and DFARS.
- Detailed user activity reports provide invaluable data for compliance audits, incident investigations, and improving security protocols
- Ensure the the confidentiality and integrity of regulated data with advanced awareness and control over where sensitive data can be transferred
- Employ the principle of least functionality by using CurrentWare to configure information systems to provide only essential capabilities
Reduce Downtime & Fight Distractions
CurrentWare’s endpoint lockdown and internet control features allow manufacturers to prioritize critical business applications and processes over non-essential activities.
- Monitor internet, bandwidth, and app use to identify potential bottlenecks and optimize network performance
- Restrict or prevent the use of nonessential programs, ports, applications, and websites
- Enforce policies that educate employees about best practices by displaying warning messages when they attempt to access potentially risky websites
Keep Legacy Systems Protected
Modernizing legacy systems is a costly and time-consuming endeavor. CurrentWare’s solutions are supported as far back as Windows 7, and AccessPatrol USB blocker is available for Windows XP on request, allowing manufacturers to ensure that air gapped legacy systems remain locked down.
- Reduce the attack surface of legacy systems by ensuring they provide only essential capabilities
- Disable functions such as internet access, WiFi, Bluetooth, and communication ports to keep legacy systems isolated
- Monitor the use of legacy systems to detect unauthorized or anomalous use
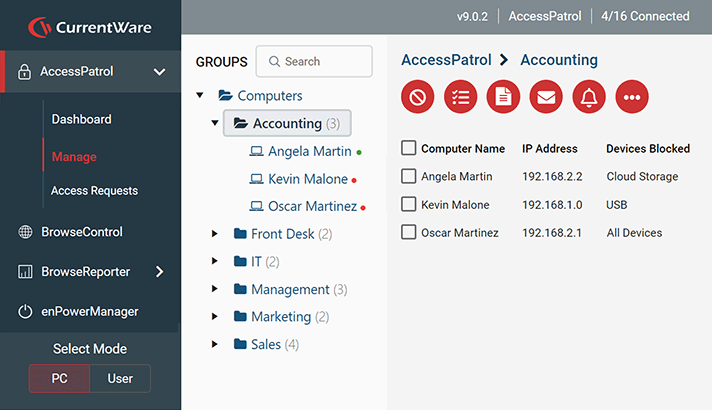
Centralized Management for Scalable Data Protection
Implement data security policies from the convenience of a central management server. Easily monitor and control your entire workforce in just a few clicks.
- Monitor & control each managed endpoint device from a central management console
- Place users/PCs in their own policy groups to apply a unique security policy to them
- Integrate with Active Directory to import & sync your organizational units or security groups to the CurrentWare Console
Manufacturing was the top attacked industry in 2021, 2022, and 2023 1
Use CurrentWare’s DLP and user activity monitoring features to detect high-risk and anomalous behavior before it escalates
The top 3 insider threat actors are staff, privileged users, and contractors
Monitor and restrict the computer activity of trusted insiders to detect and prevent insider threats before they cause damage
Over half of organizations have experienced an insider threat from 2022-2023 2
Third-party vendors and employees with privileged access to internal systems present a significant risk to manufacturers
See What Our Customers Have to Say
The reports are very easy to understand and the fact that they can be emailed to you on a schedule is amazing, and have made finding productivity killers VERY easy. Customer support has been fantastic every time I've had to reach out to them; I highly recommend them!
Kristen S, Associate IT Director
The Coding Network, 700+ Employees
As a 'novice' I was able to set up with help from support in about an hour. Previous software took forever and didn't work as advertised. This software worked right out of the box.
Dr. Gerard B, Office Manager
Medical Practice, 2-10 Employees
In my nearly 40 years in the IT business I’ve worked with a lot of support teams. I really appreciate CurrentWare going the extra mile to help me get the most out of the product. They’ve definitely outweighed any of the other competitors that I’ve looked at.
J.S, Managed Services Provider
Vehicle Dealership, 150-200 Employees
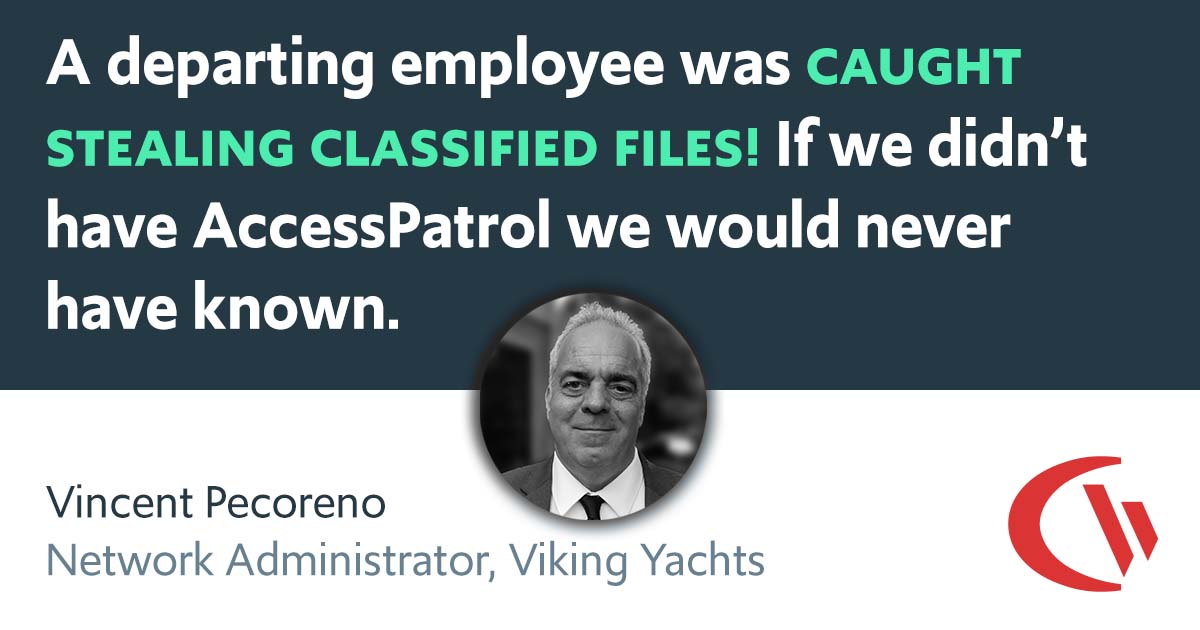
We have experienced data leaks by dishonest employees in the past and [CurrentWare's] AccessPatrol has helped us avoid them and work with greater security and peace of mind for us and our customers.
Julio V, Head of Information Technology
Financial Services Industry, 10,001+ employees
Expand your capabilities with CurrentWare's award-winning productivity and security software



CurrentWare's Key Features
User Activity Monitoring
Track web browsing, software use, search queries, and more
Screenshot Monitoring
Take automatic screenshots or remotely view desktops
Track Software Usage
Get insights into software usage trends in your organization
Transparent & Stealth Modes
Run silently in the background or provide notice of monitoring
Block USB & Other Devices
Set full access, read only or no access on storage devices
Device Whitelist
Allow only authorized storage devices to be used
Block File Transfers
Prevent files from being transferred to portable storage
DLP Activity Reports
Track file transfers, storage device use, file operations, and more
Block Websites
Block websites based on
URLs & content categories
Block Downloads/Uploads
Prevent uploading and downloading based on file type
Application Blacklisting
Block specific Windows
applications from launching
PC Power Management
Remotely track and control PC power states
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server
1 IBM. (2024). (rep.). X-Force Threat Intelligence Index 2024. Retrieved from https://www.ibm.com/reports/threat-intelligence.
2 Cybersecurity Insiders – 2023 Insider Threat Report | https://www.cybersecurity-insiders.com/portfolio/2023-insider-threat-report-gurucul/