How to Use Computer Spy Software for Employee Monitoring & Security

Would you like to use computer spy software to monitor employees in your workplace? CurrentWare’s remote PC monitoring software can be deployed in visible or hidden mode, allowing you to track computer activity of employees.
- Monitor employee productivity with activity logs of browser history, application usage, desktop screenshots, and other online behavior
- Record browser activity to enforce acceptable use policies for your computer network and ensure appropriate online behavior
- Track USB connections and use the USB file activity tracking features to stop potential data breaches
- Monitor network bandwidth usage to identify bandwidth hogs
- Keep captured data on-premises for optimal data protection
In this article, you will learn how to use computer monitoring software to spy on what a user does in their web browser, the types of reports offered by CurrentWare’s computer monitoring software, and how to get a free trial to install on the device you want to track and control.
Learn More: CurrentWare’s computer monitoring software features
FREE WHITE PAPER
Best Practices for Monitoring Employees
In today’s privacy-conscious world employers need to monitor employees in a way that is transparent, minimally invasive, and respectful of employee privacy.
Want to use monitoring tools to get instant visibility into employee productivity, engagement, and PC usage? Read this white paper to learn the best practices for monitoring employees in the workplace.
Looking for internet control and computer monitoring software for a Windows PC?
With CurrentWare’s award-winning productivity and security software, you can:
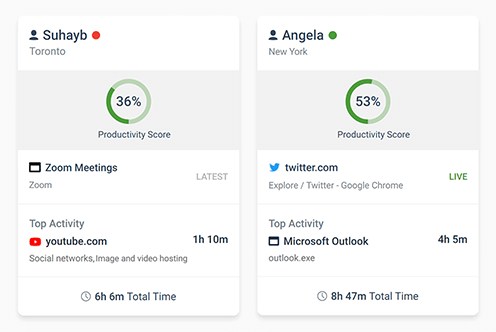
- Track Employee Productivity: See if work hours are spent on social media or work-related tasks
- Control Internet Connection: Block websites on any web browser
- Track Websites Visited: See what websites are visited, how long the user was browsing, and if they were actively using the website
- Capture Screenshots: Record automatic screenshots when your user visits a specific website or uses a specific app
- Stealth Mode: Install the Windows spy software with the stealth or transparent modes enabled to meet your privacy requirements.
- User & Computer Monitoring: Get reports on a target computer and specific computer users. Review aggregated data or see exactly which user is responsible for bandwidth abuse and low productivity
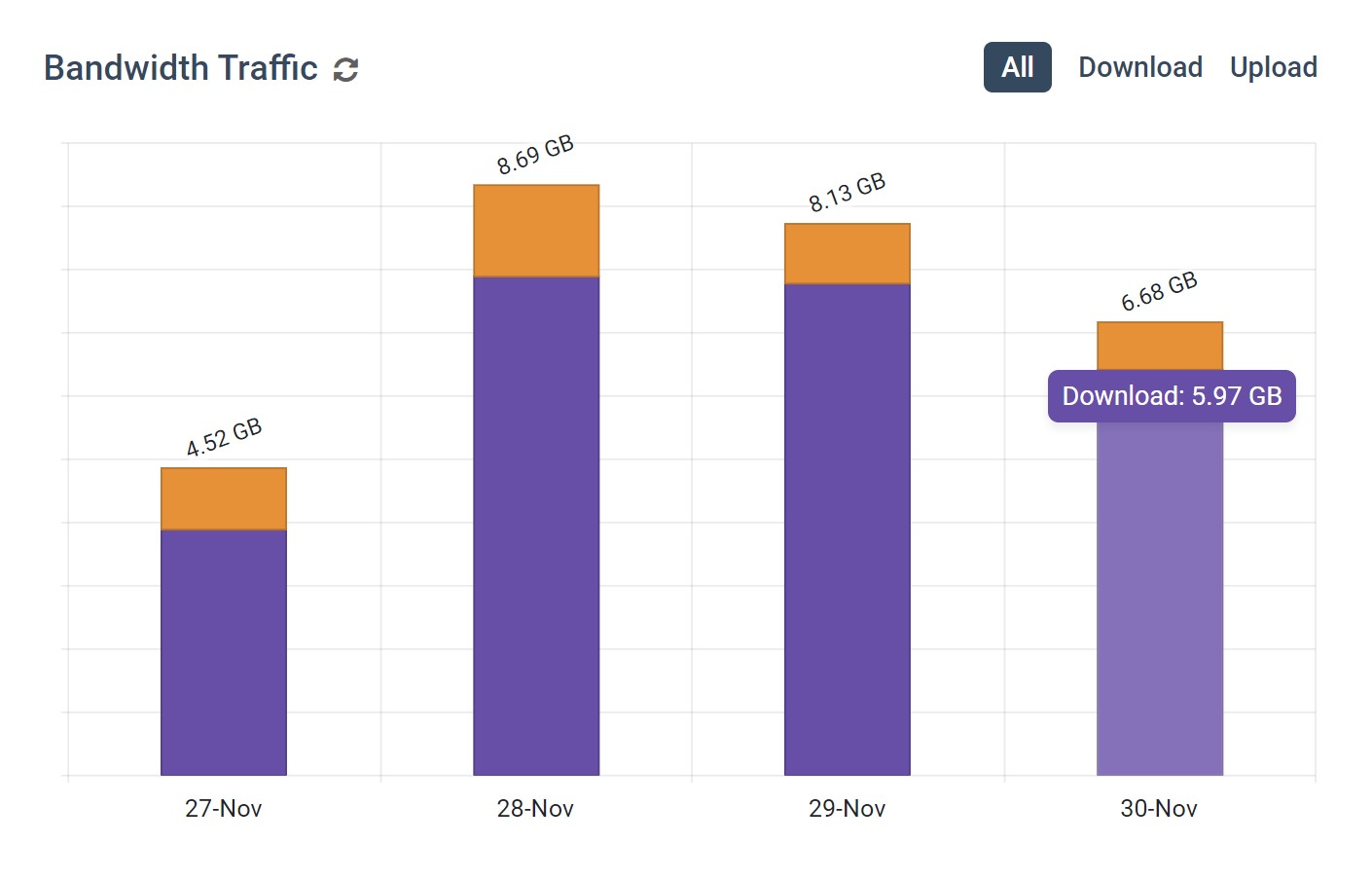
- Bandwidth Monitoring: See how much data is sent and received by each computer and user to diagnose network speed issues and identify bandwidth hogs that interfere with computer network connections.
What Is Computer Spy Software?
Computer monitoring solutions can be split into two distinct categories: Computer programs that allow designated administrators to track computer usage on their managed devices, and malicious spyware programs that are used to unknowingly exfiltrate data on infected systems.
Non-malicious spy software for PC can be used by an employer to monitor a employee that is using a company-owned computer. Stealth monitoring (incognito monitoring) is used as a proactive protection measure for alerting managers and security personnel to unlawful or dangerous behaviors of their employees without making the computer monitoring system visible to them.
Spy software for PCs can be deployed remotely via company servers to the devices that will be monitored, allowing for the software to be distributed to remote workers. With stealth monitoring features enabled on the program, users will not be aware that computer monitoring is taking place.
The preference for stealth monitoring vs transparent monitoring in a given workplace is dependent on the culture of the company, applicable legislation, and their employee computer monitoring goals.
Examples of Stealth PC Monitoring Software
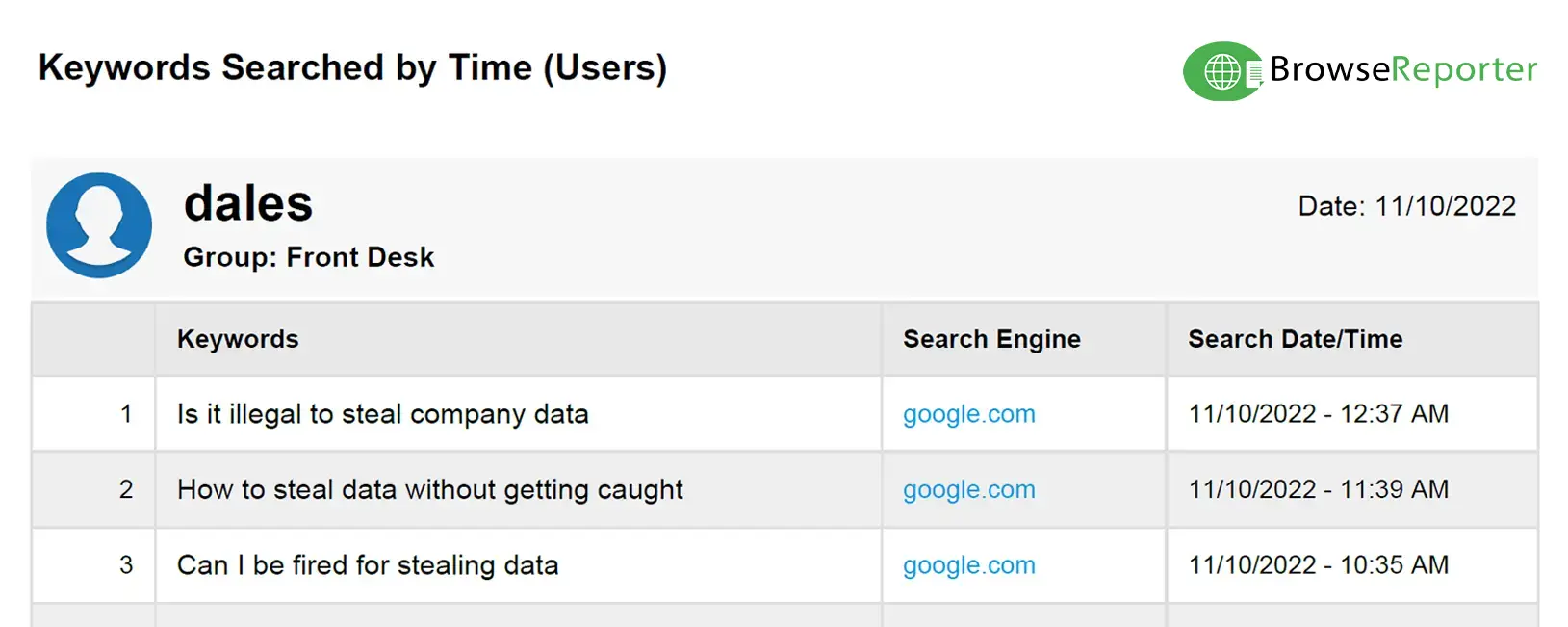
- Internet Usage Monitors: Software for monitoring internet activities that tracks websites visited, bandwidth consumption, search keywords, and the time spent on the web. These softwares are often used to identify personal internet browsing during work hours.
- Employee Monitoring Software: Tools used by managers to increase productivity, detect insider threats, collect evidence of misconduct, and protect computers against misuse. These features often come with features for alerting designated personnel to suspicious or undesirable activity.
- Endpoint Security Software: These types of software track how users interact with the devices and the files they have access to. Endpoint monitoring tools are used by businesses as a proactive method of endpoint protection to ensure that data accessed by devices is kept safe.
- Spyware: Malicious programs used to secretly record devices and steal data. These programs come with features that are used for espionage and data theft, such as a keylogger to capture every keystroke; keyloggers are often used to remotely spy on online conversation and steal passwords.
Is Computer Spy Software Legal?
In the US and Canada, employee monitoring is generally perfectly legal as a method of ensuring that company assets are protected and used responsibly. Depending on legislation related to your jurisdiction and industry there may be additional legal requirements surrounding topics such as informed consent from employees, establishing a legitimate business need, and protecting employee monitoring data.
How to Use Spy Software for PC Legally
- Informed Consent: Even if the Windows spy software itself will be running discreetly, the best practice is to forewarn monitored users that monitoring measures are taking place. To demonstrate that informed consent has been achieved, written acknowledgments of acceptance for monitoring policies should be maintained.
- Legitimate Need: When implementing spy software for your PCs, you must ensure that the tracking that is taking place has a legitimate business use. Excessive monitoring without a valid basis may be considered a violation of privacy-related legislation.
- Proportionality: After establishing your legitimate business needs for monitoring employees, you should review the benefits of the solution against the privacy impact on your employees. If less invasive monitoring measures can achieve the same results, it is best to adjust your monitoring method accordingly.
- Appropriate Use: Just as you need a legitimate need to monitor employees, you must also ensure that the data captured with informed consent is used responsibly and for the purpose for which the consent was provided. If you intend to use a computer spy program to ensure that technology and related assets are used appropriately, that same data should not also be used in performance appraisals.
- Data Protection: Employee monitoring data should be treated as highly sensitive and secured appropriately. Depending on the features of the spy software, there may be screenshots, sensitive search queries, or browsing history that is sensitive.
- Personal Devices: If your workplace allows employees to use personal devices for work, known as “Bring Your Own Devices” (BYOD), these devices should not be monitored, as there is a high risk to the privacy of the user.
- Remote Monitoring Software: If the monitoring software is intended for remote workforce management, the tracked devices must be company-owned. As an alternative, remote monitoring software that tracks how users interact with the company network through remote access methods, such as a VPN, could be used.
Workplace Monitoring Policy Template
- Disclose your company’s intent to monitor employees in the workplace
- Set workplace privacy expectations for employees
- Meet transparency requirements for compliance with privacy laws
Get started today—Download the FREE template and customize it to fit the needs of your organization.
Computer Spy Software for PC
CurrentWare’s award-winning computer monitoring software BrowseReporter, allows you to remotely monitor a target PC from a convenient central console.
To get started, simply sign up for the the free trial, install the monitoring solution’s central console on the manager’s computer, then install the agent on the target computer. From the console you can use the software to monitor and control each monitored computer in your network.
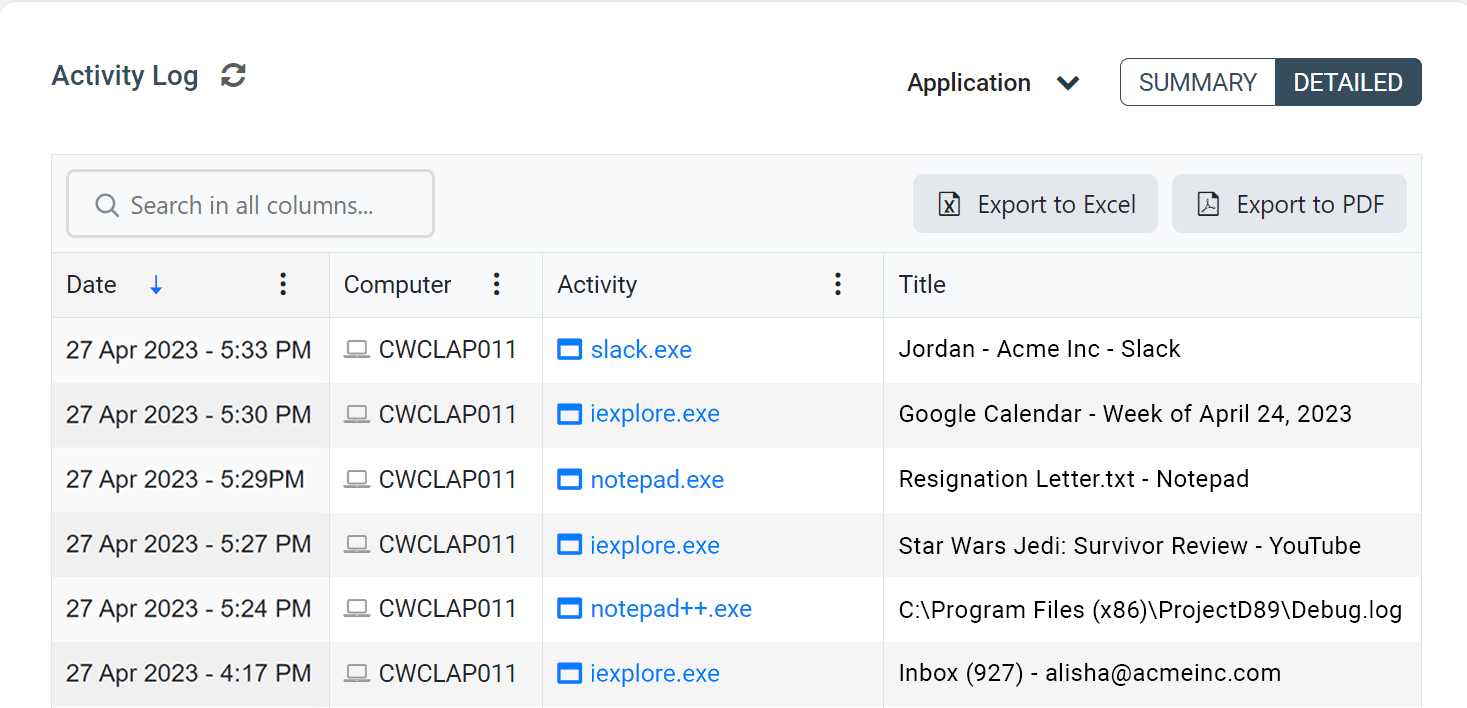
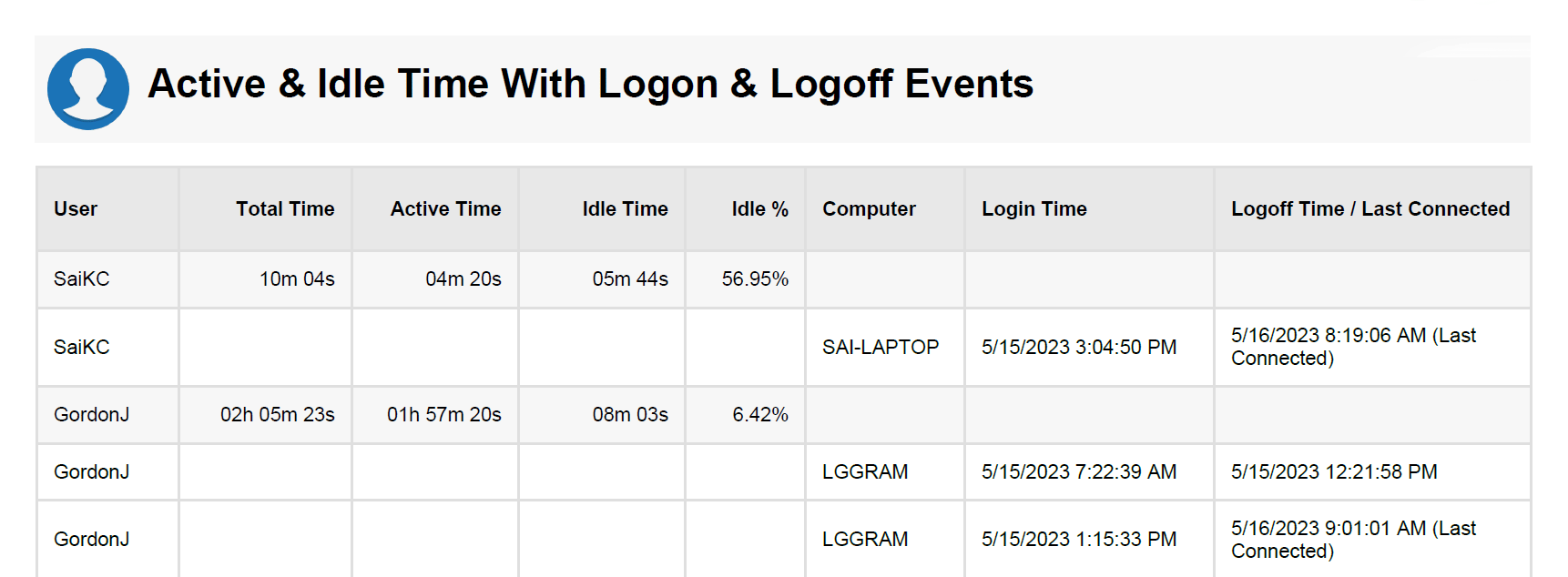
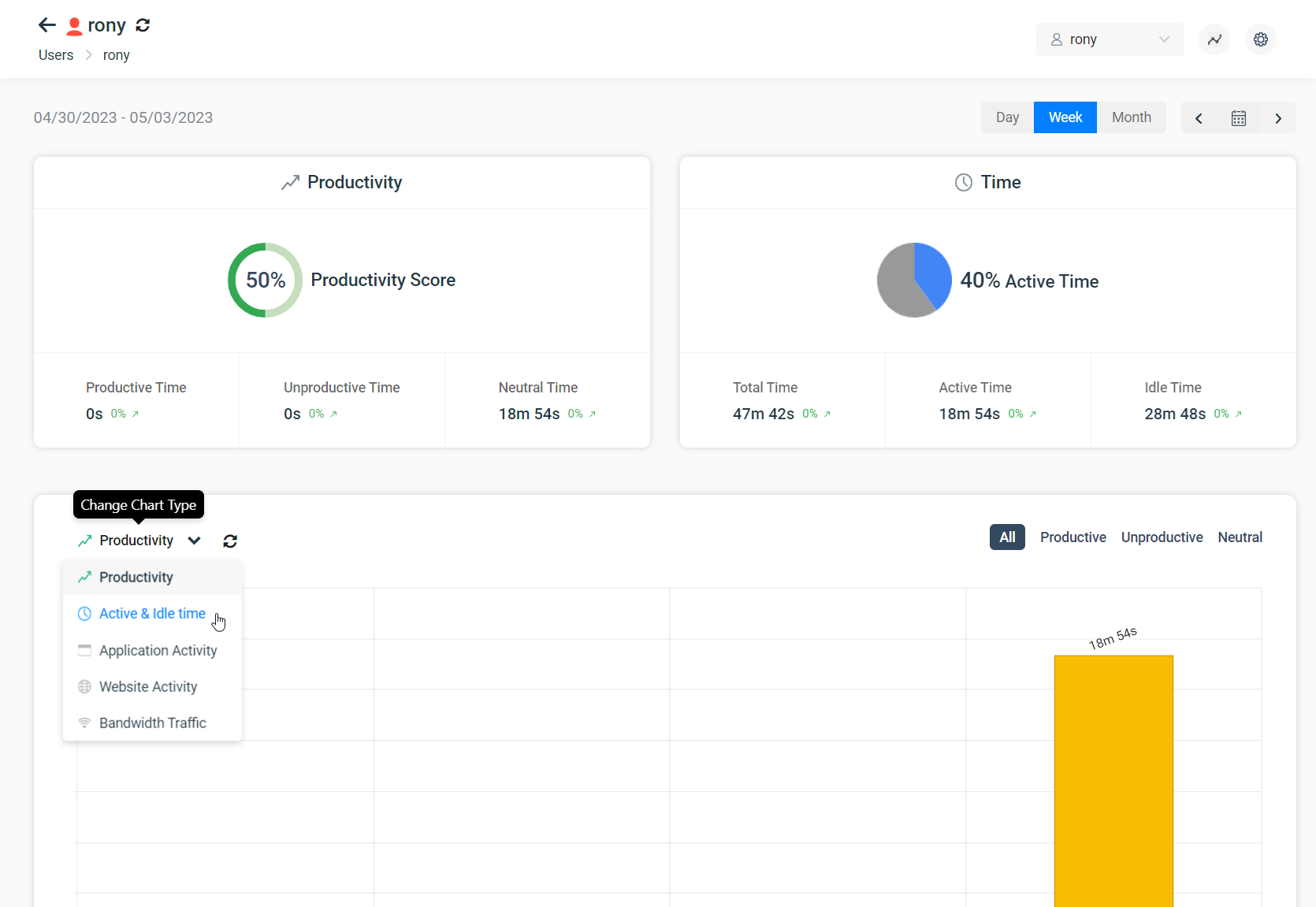
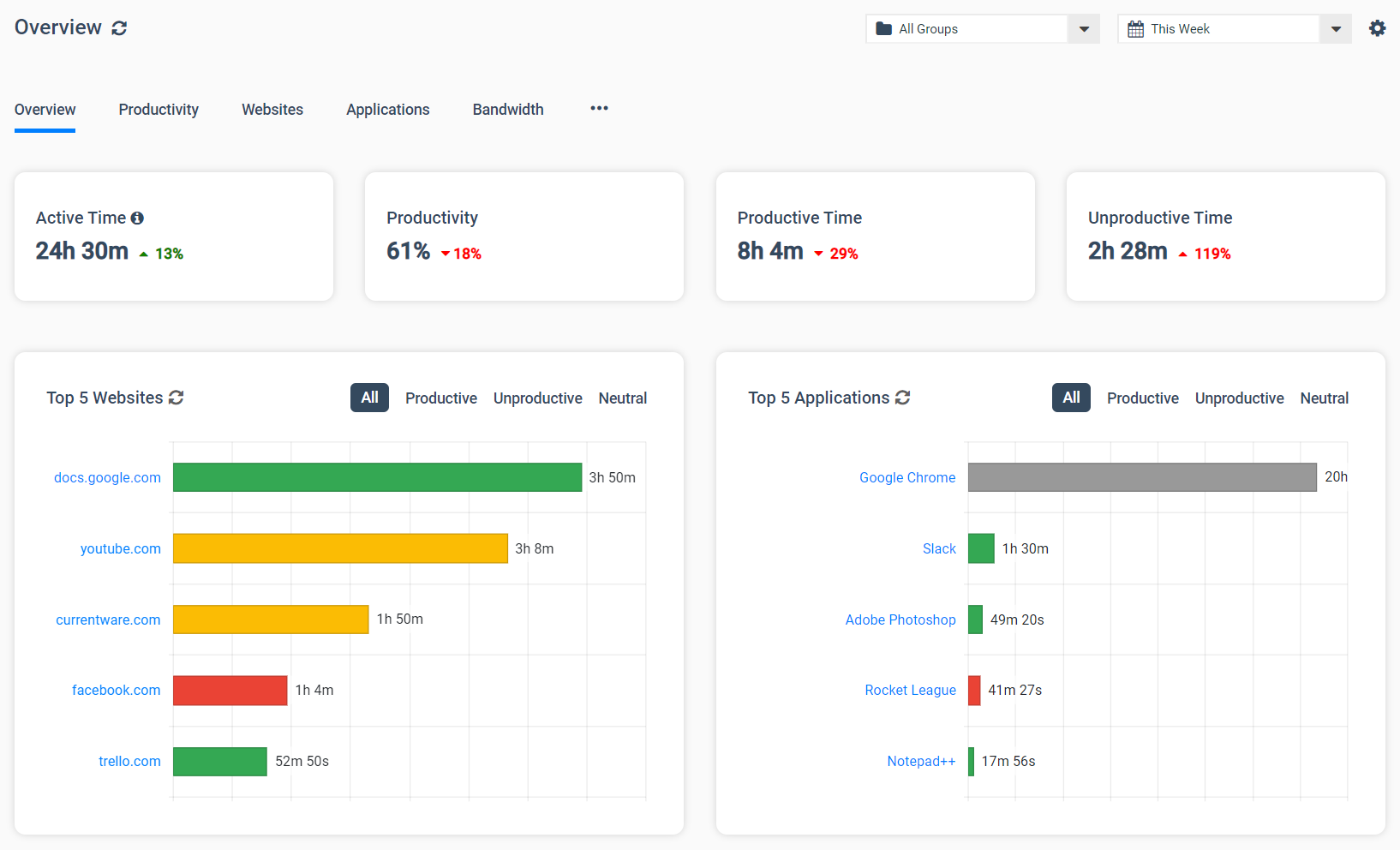
BrowseReporter’s online and computer activity reports show you what your users are doing on their computers. You can review their web history, see what apps were used on their computers, and continue remote monitoring and control even when your users move to a new location.
Note: BrowseReporter can be installed on a Windows device, terminal server, or Citrix virtual desktop. It is not suitable for Mac monitoring at this time. To use it on a Mac computer, you need to install it on a Windows VM. For the most up-to-date information, please refer to our system requirements
Track Websites Visited & Other Online Activity
Take Screenshots of User Computer Screens
BrowseReporter’s remote screen capture feature can be used for taking screenshots when specific apps or websites are used. That way, you can see exactly what was on their screen at the time.
Frequently Asked Question (FAQ)
Conclusion
Remote computer monitoring can be an effective tool for time tracking, detecting unsafe internet browsing, and ensuring that employees are using their devices appropriately. So long as the monitoring takes place with privacy and transparency at the forefront, your in-house and remote workers can be monitored as part of your productivity and data security strategy.
Improve Employee Productivity With
CurrentWare’s Remote Employee Monitoring Software
Ready to get advanced insights into how your employees spend their time? Reach out to the CurrentWare team for a demo of BrowseReporter, CurrentWare’s employee and computer monitoring software.
- Improve Productivity
Track unproductive web browsing and idle time to detect time-wasting - Save Time With Intuitive Reports
User-friendly reports make it easy to understand employee computer activity - Enhance Visibility
See how employees spend their time—even on Terminal Server and Remote Desktop Services!