What is Keylogger Software and Should You Use it on Employee Computers?

When faced with employee productivity and insider threat challenges, many businesses may opt to use a keylogger to monitor their employyes.
However, keyloggers bring forth many challenges and concerns, and there are less invasive and more secure alternatives that provide more valuable insights.
In this article, we will weigh the pros and cons of keyloggers, while recommending alternatives to keyloggers that will improve the productivity and security of your company without the security and privacy risks associated with logging individual keystrokes.
What is a Keylogger?
As the name suggests, keyloggers—also known as keystroke loggers or keystroke monitoring tools—are a type of monitoring software or hardware that records the actions of the computer user by logging the various keys and buttons that are pressed on the keyboard.
While keyloggers have legitimate uses such as software/hardware testing, capturing keystroke dynamics data, and corporate user activity monitoring, these tools are typically used by threat actors to capture passwords and other sensitive information that they can leverage in an attack.
Also Read: CurrentWare MSP Webinar
Types of Keyloggers:
Keylogger Software
Software keyloggers are programs or apps for monitoring keystrokes on a device. Keylogger software can be used to capture keystrokes on a mobile phone or a desktop computer.
As they are a software solution these programs can be discretely installed without physical access to the target device. This makes keylogger software the most common keylogging method that threat actors use to capture personal information, credit card details, clipboard contents, and other sensitive information.
Installed onto the computer’s hard drive, either legitimately or illegitimately, the keylogger software sends logs to a third-party computer or server through email or file transfer protocol.
How difficult a software keylogger is to detect and what it captures will vary depending on which layer it captures keystrokes. A software keylogger can be implemented in a hypervisor, the kernel, an API, web forms, through Javascript, and memory injection. | Learn More
| Advantages of Keylogger Software | Disadvantages of Keylogger Software |
| Easy to deploy at-scale | Often flagged by antimalware software as malicious |
| Inconspicuous user activity monitoring | Incapable of logging BIOS inputs |
| Can be deployed without physical access to the device you would like to record keystrokes on. |
Keylogger Hardware
A hardware-based keylogger is typically a peripheral that can be installed in line with the keyboard’s connector. These keyloggers are designed to have an innocuous appearance, making it difficult to detect by users that are not familiar with the devices. A hardware keylogger may also be installed within the keyboard itself, making detection far more difficult.
To access the keystroke log the administrator of the keylogger will typically need access to the computers, making the retrieval of keystroke logs much more difficult to manage when compared to keylogger software.
Unlike keylogger software which can often be detected by anti-spyware software, keystroke logging hardware can only be intercepted by physically removing it from the target computer.
While this type of keylogger is typically a peripheral, there have been other varieties such as a proof-of-concept method where the electromagnetic emissions of a wired keyboard have been captured wirelessly from up to 66 feet away.
| Advantages of Keylogger Hardware | Disadvantages of Keylogger Hardware |
| Does not require any software to be installed on the target user’s computer | Requires direct access to the target device, making remote management impossible |
| Can record BIOS keystroke inputs | Typically needs to be installed in-line with the keyboard, making it easy to detect |
What Are Keyloggers Used For?
Maliciously Logging Sensitive Records
Although there are many legitimate cases for the use of keyloggers, the technology is more commonly known for its use throughout the cyber-criminal underworld. In fact, 60% of phishing scams contained some form of keylogging technology, making keyloggers one of the most widely used tools in malware attacks.
Threat actors will use keylogger programs to collect sensitive records such as passwords, payment information, and personally identifiable information (PII). This information may be used to escalate an existing attack or enable attacks from other threat actors.
Also Read: An Overview of Ransomware Attacks: Trends and Threats
Insider Threat Detection
A 2020 report from IBM and ObserveIT found that insider threats cost organizations $11.5 million on average. This is a 30 percent increase from 2018, indicating that insider threats are becoming more and more prevalent in business.
High-security organizations such as those in the national defense industry may monitor their employees for signs of insider threats with keyloggers. They can use a keylogger to detect anomalous behavior such as a WPM cadence that far exceeds what is typical (a potential indicator of a malicious script executing) or the presence of high-risk keywords.
Evaluating Data Entry
Data entry positions require the worker to input a high volume of data from multiple sources into a database. Generally, the information inputted into the database contains customer and account information in the form of alphabetic and numeric information that is entered through the keyboard.
Given the demand for a high volume of data entry from their employees, many companies opt to monitor employee productivity through keyloggers. By capturing the volume of data entered into the database through the employee’s operating system, managers can determine whether or not individual workers are hitting their quota.
As most data entry jobs require a minimum of 45 words per minute entered into the system, an employer can utilize keylogging technology to ensure that its workers are maintaining this standard of production.
To reduce the cybersecurity risks of logging keystrokes an organization may opt for a keylogger that does not monitor individual keystrokes. Instead, they may use software that simply detects whether or not any input was registered.
Also Read: Are You A Victim of Facebook Fatigue?
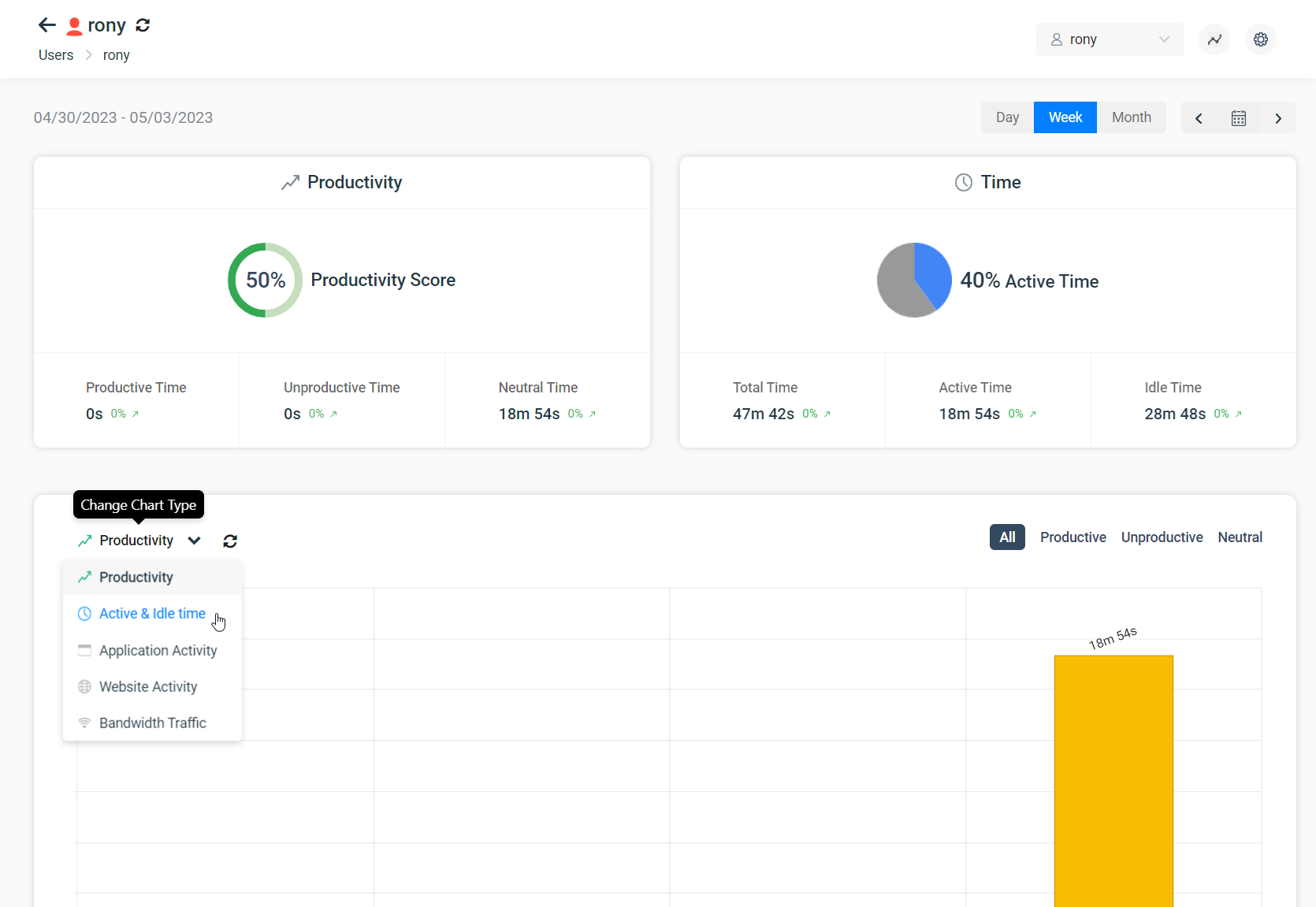
Productivity Monitoring
Productivity monitoring is a focus in most businesses. Businesses that want to monitor productivity may monitor internet activity, record keystrokes, take screenshots of desktops, or track idle time.
With as much as 64% of employees visiting non-work related websites every day at work, employers are often incentivized to implement tools that detect disengagement.
That said, recording individual keystrokes puts the company at risk of capturing sensitive personal information such as private messages and passwords.
With keyloggers, employers can see every last keystroke that their workers are typing. While this could theoretically be used for productivity monitoring, the sheer quantity of data and the potential to capture sensitive information make a keylogger an ill-advised method for monitoring employee productivity.
So, what’s a better way to prevent employees from wasting time at work?
Employee internet monitoring software is the perfect solution for recording the websites that employees visit, tracking what apps are used, and evaluating how much time is spent on activities that are considered productive for your organization.
When employers monitor productivity, they are often looking for behaviors that are considered to be unproductive such as spending time playing games, browsing social media, or engaging in other activities that do not directly benefit the business.
Rather than taking the risks that come with capturing individual keystrokes, internet monitoring software offers a privacy-conscious option for enforcing acceptable use policies and monitoring user activity.
Concerns With Keyloggers
Legal
Monitoring individual keystrokes is highly invasive. As these employee monitoring methods risk directly capturing sensitive personal information employers are seldom justified in using them over less-invasive methods such as computer activity tracking software.
Naturally, the legality of recording individual keystrokes will vary from one jurisdiction to another. As a best practice employers must evaluate other options to determine whether or not they truly want to monitor keystrokes or if their goals can be met with less invasive monitoring methods.
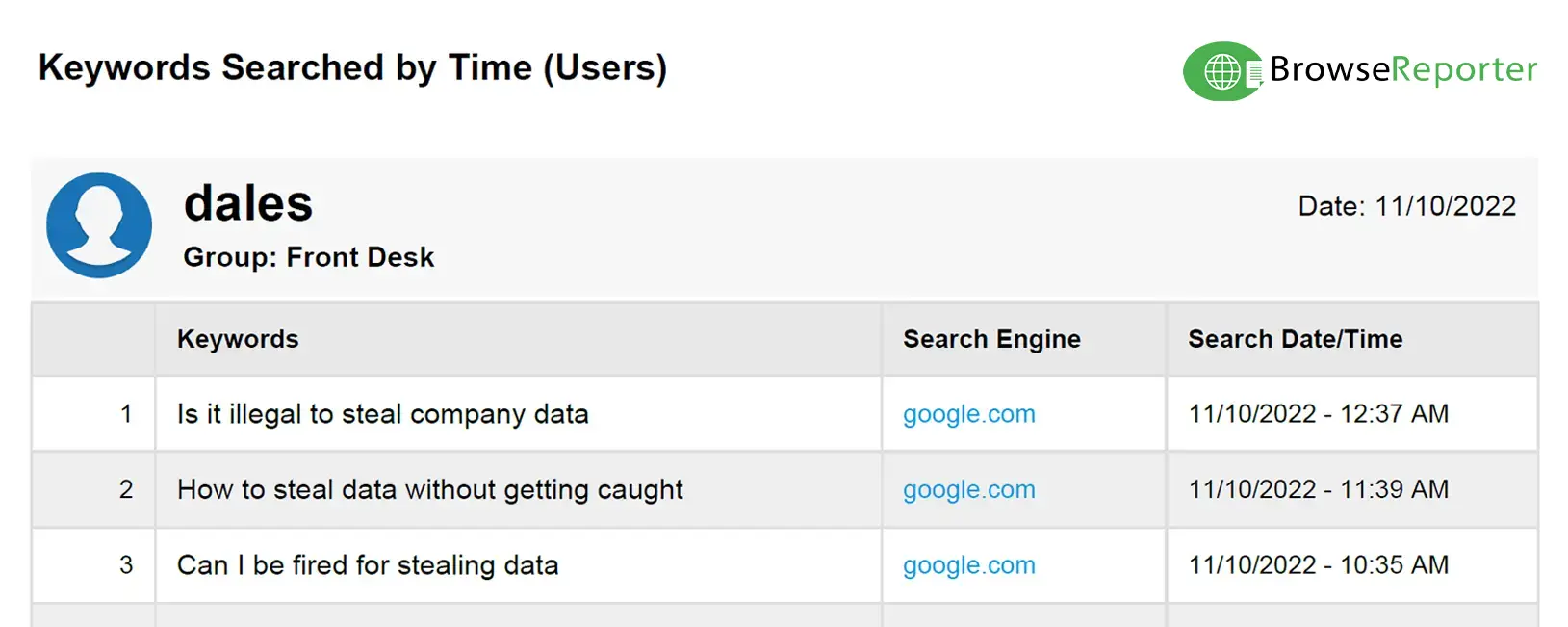
Even in jurisdictions where keyloggers are permitted, how the logs are handled can raise legal concerns. Since keylogging technology can capture sensitive information such as a user’s passwords, private messages, or other forms of personal information, this data must be adequately protected from misuse with administrative and technical safeguards.
For example, if an employee is unaware of the keystroke logger, they may reveal personal information via a chat or email with a family member or friend. This type of information can be highly sensitive, and if mishandled, can lead to legal consequences for the administrator.
Also Read: What is a Data Breach? (Infographic)
Data Overload
The average typing speed is around 40 words per minute (WPM). If a given user is writing for an hour straight they will output an average of 2400 words for each hour they write.
Times this by the number of employees in the organization and it’s immediately evident that a keylogger is going to generate ludicrous amounts of data; far more than is useful in most circumstances.
While the actual storage space required for keyloggers is negligible, from a logistics standpoint the sheer volume of information is overwhelming for administrators to effectively manage and interpret.
While artificial intelligence can be trained to interpret this data, this level of sophistication far exceeds what an average business truly needs in an employee monitoring solution. For example, if a business wants to see how much time is spent browsing the internet they can simply use internet monitoring software to run a report on the employee’s internet activity.
Cybersecurity Risks
The databases of keyloggers are an attractive target for hackers as credit card information and passwords are highly valuable commodities within the cybercriminal underworld.
From an insider threat management perspective, a disgruntled administrator with access to the logs is a significant threat. They could opt to sell the records to an external threat actor or simply browse the logs for passwords and other sensitive information.
Also Read: BrowseReporter Employee Monitoring Software
The Best Alternative to Keyloggers for Employee Monitoring
Throughout this article, we have touched on the practical usage of keyloggers while also highlighting the many flaws that the technology inherits.
Considering the legal and administrative concerns that arise with the implementation of keyloggers, along with concerns regarding the practical effectiveness of the technology, monitoring software alternatives should be examined by businesses looking to increase security and improve productivity.
The most effective way to improve employee productivity and increase network security is through the use of employee computer monitoring software.
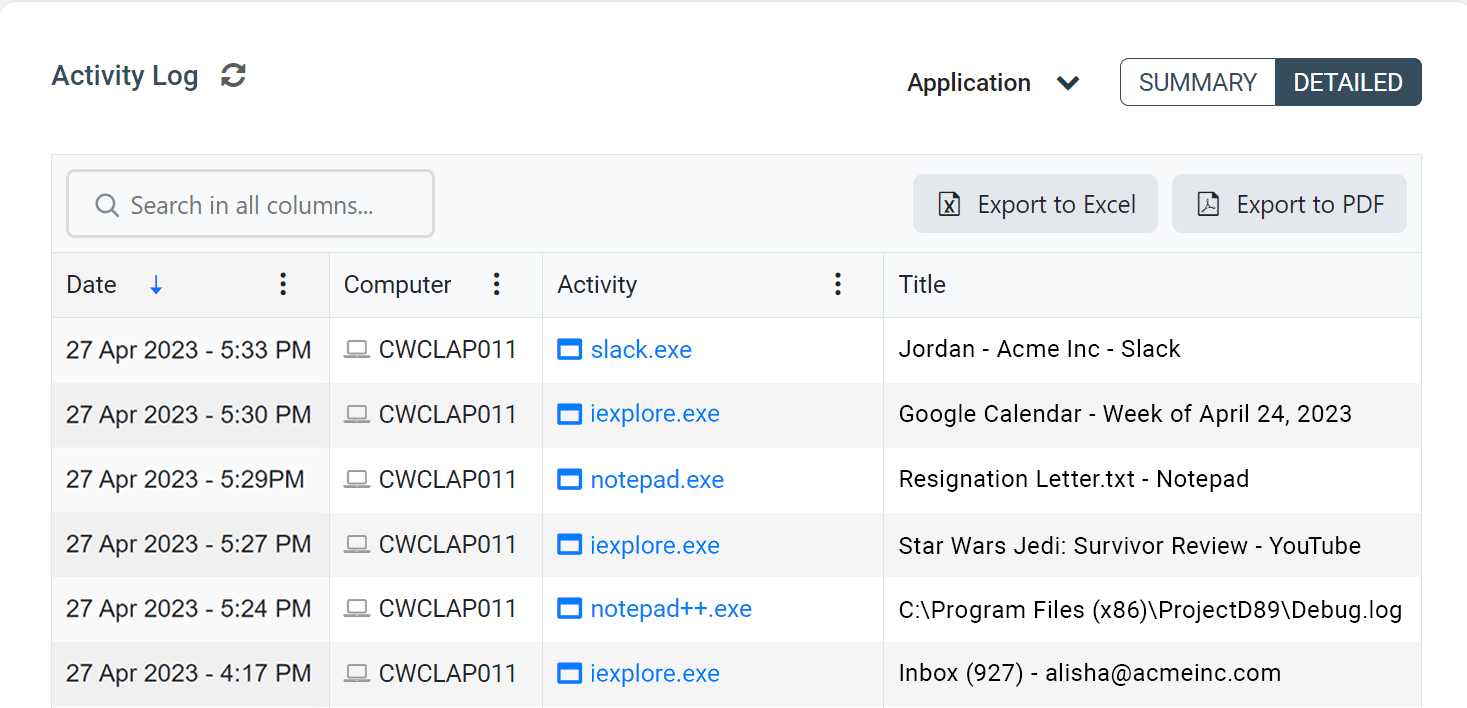
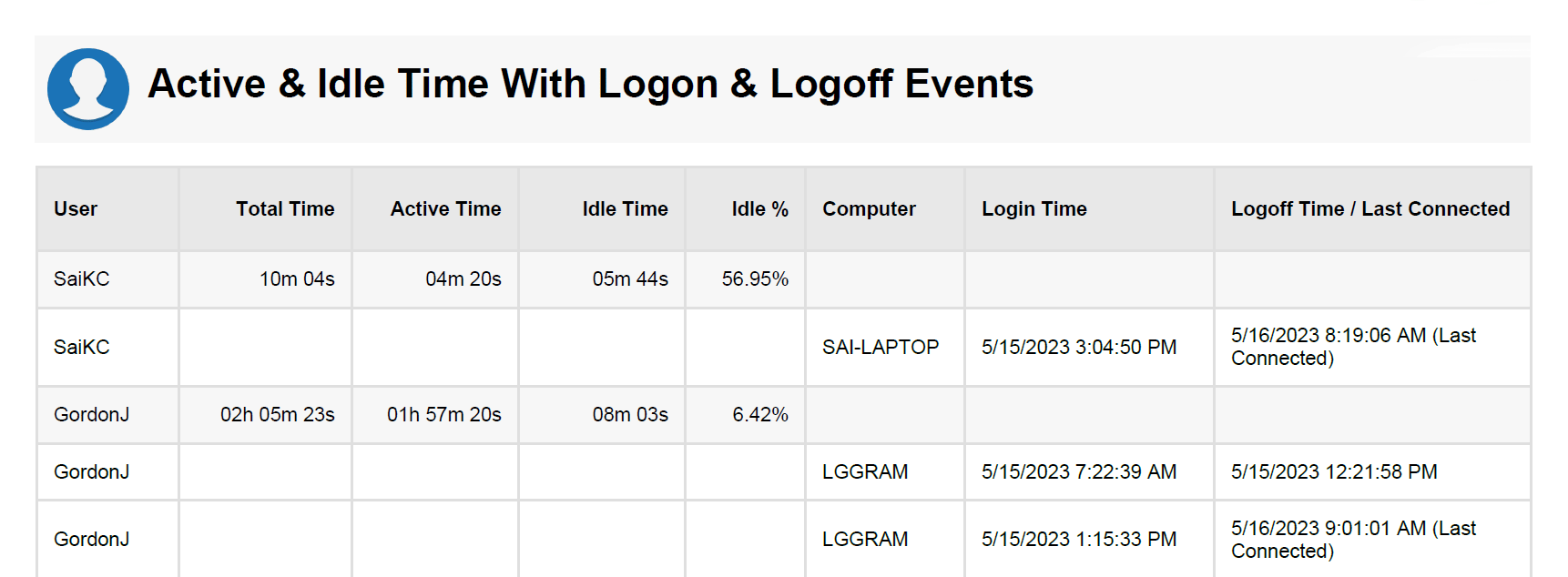
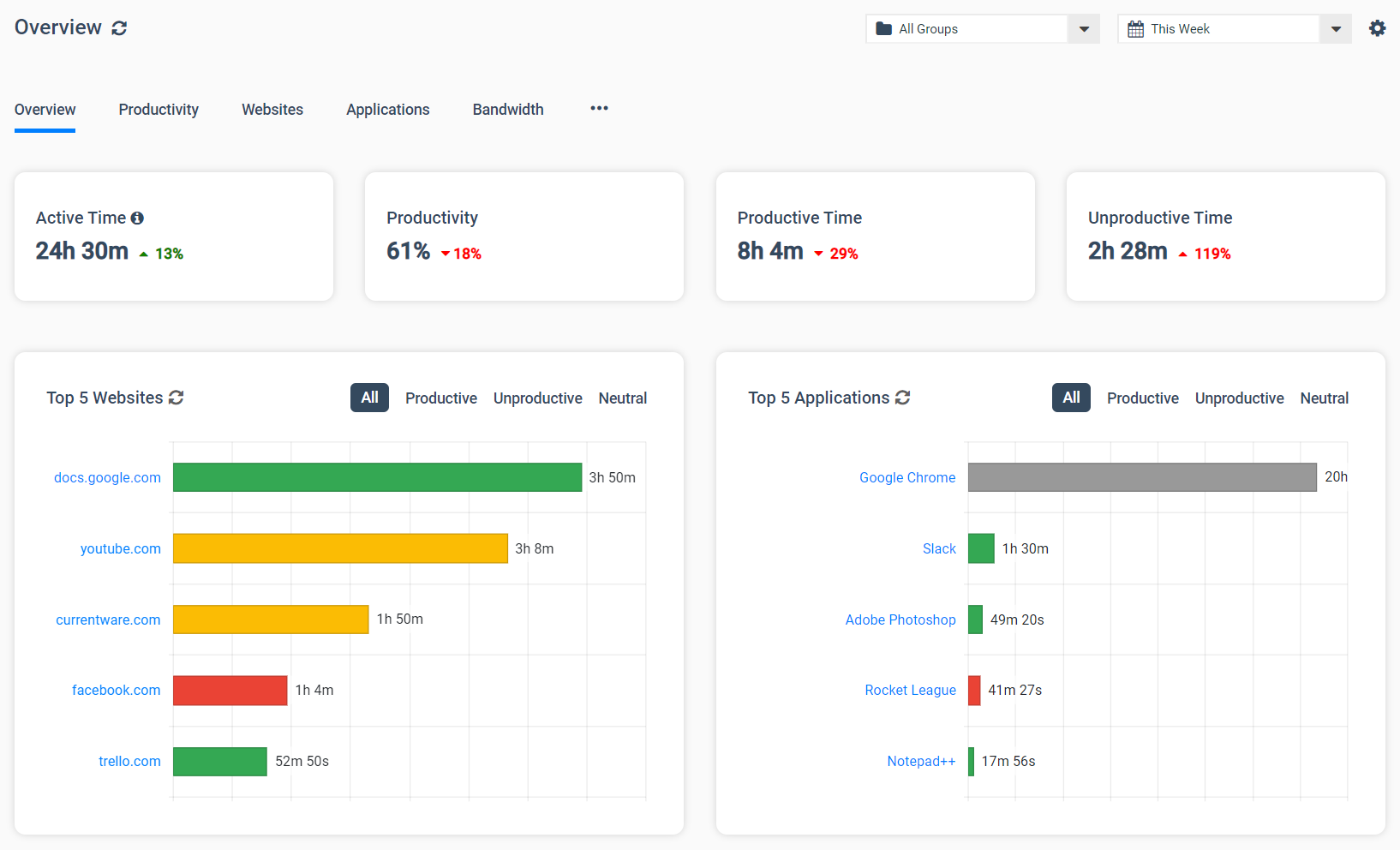
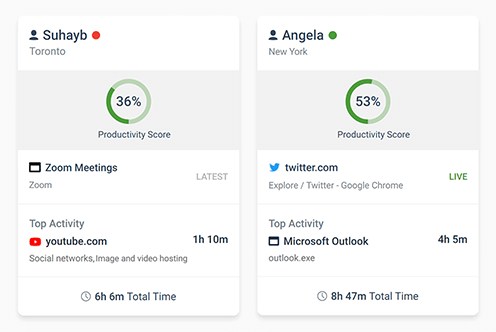
BrowseReporter is an easy-to-use solution for tracking the productivity and efficiency of individual employees or an entire workforce. Its computer usage reports can track internet activity and application usage, providing managers with the insights they need to make data-informed productivity management decisions.
These reports automatically filter out noisy background data such as CDNs, giving an accurate and easy-to-understand overview of employee computer usage.
BrowseReporter can be easily accessed by administrators through the central web console, providing convenient access to the records of your entire workforce.
Improve Employee Productivity With
CurrentWare’s Remote Employee Monitoring Software
Ready to get advanced insights into how your employees spend their time? Reach out to the CurrentWare team for a demo of BrowseReporter, CurrentWare’s employee and computer monitoring software.
- Improve Productivity
Track unproductive web browsing and idle time to detect time-wasting - Save Time With Intuitive Reports
User-friendly reports make it easy to understand employee computer activity - Enhance Visibility
See how employees spend their time—even on Terminal Server and Remote Desktop Services!