Remote Desktop Monitoring Solutions for Secure and Productive Work Environments

Use CurrentWare’s remote desktop monitoring software to audit logons, internet activity, application usage, and USB activities of your remote users.
Remote desktop solutions are becoming increasingly common with the prevalence of distributed workforces. With employees working from home now more than ever your organization needs to ensure that remote desktop activities are monitored for security, productivity, and compliance purposes.
In this article you will learn how to use CurrentWare’s remote PC monitoring software solutions to audit the activity of users that are using remote desktop, virtual machines, Citrix, and other Windows-based remote access and virtualization technologies.
Want to learn more about monitoring user activity in a Citrix environment? Check out this article on Citrix user activity monitoring with CurrentWare
Table of Contents- Why Audit Remote User Activity?
- What CurrentWare’s Remote Desktop Monitoring Software Tracks
- Track Remote Employee Work Hours (Audit Logon Events)
- Remote Employee Productivity
- Internet and Application Usage
- Bandwidth Consumption
- Active vs Idle Time
- Audit File Transfers to Portable Storage Devices
- How Remote Desktop Monitoring Software Works
- Remote Desktop Monitoring Software FAQ
- Get My Free Trial
Why Audit Remote User Activity?
Note: The above video showcases a legacy user interface for BrowseReporter. To see the most up-to-date features and interface please visit the BrowseReporter product page
Meet Security Compliance Requirements
Remote desktop monitoring software keeps a detailed history of users who have connected to the corporate network, along with their usage details. These reports are valuable security tools for compliance and auditing purposes. In the event of a data breach the activity of users can be audited for high-risk, anomalous, and suspicious activity.
CurrentWare’s central console ensures that you have the most important user activity data accessible from one place, allowing you to generate user activity reports easily. Reports can be generated on-demand, at a set schedule, or when specific activities occur.
Detect Insider Threats
User activity monitoring is an essential part of mitigating insider threat risks. This is especially true when users are allowed to access internal resources from outside of the network.
By auditing remote user activity you can detect high-risk and anomalous activities such as large file transfers to USB storage devices, inappropriate internet usage, and the use of unsanctioned applications.
With CurrentWare’s monitoring software you can leverage detailed user activity monitoring reports to enhance your insider threat detection strategy.
Also Read: Managing a Hybrid Workforce: The Role of Employee Monitoring Software
Monitor Remote Employee Productivity
When employees work from home (or other remote locations) there is far less visibility into their work habits than when they work in the office.
Remote desktop monitoring software tracks the activity of these employees to ensure that working hours are being used efficiently. Depending on the needs of your environment you can monitor employee productivity while they are connected to a Windows terminal server, a remote workstation, or their local device.
Dedicated monitoring software keeps all internet browsing data intact so that users cannot hide their internet usage by deleting their history.
If excessive unproductive web browsing and application usage is detected, you can address this productivity concern before it escalates.
Enforce Acceptable Use Policies
Company policies are valuable tools for communicating security, decency, and productivity standards to end-users. Monitoring computer activity with remote desktop monitoring software ensures that these policies are being followed.
With the monitoring software in place you will be alerted to any instances of misuse, allowing you to provide remote employees with appropriate corrective actions.
Also Read: How to Monitor Remote Employee Activities with Citrix Employee Monitoring
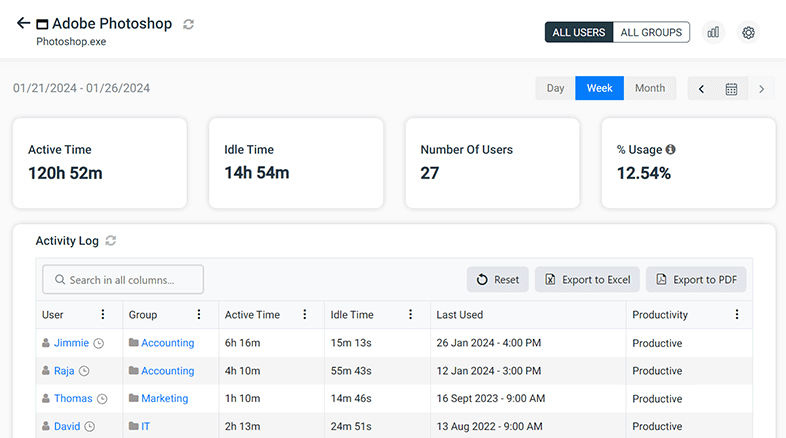
Track Software License Usage
Did you know that underutilized software cost businesses a staggering $34 billion per year? Monitoring employee application usage allows you to track the utilization rate of software so you can avoid paying for software that isn’t being used.
CASE STUDY
Activity Insights in Citrix Workspace Drives Software Adoption and Productivity
What CurrentWare’s Remote Desktop Monitoring Software Tracks
CurrentWare audits user activity on local or cloud-based desktop computers, virtual machines (VMs), and servers running the Windows operating system.
When monitoring and managing your end-users in Citrix with CurrentWare you can track and control computer activities with PC Mode to manage the individual virtual machine or with User Mode to track and control the activities of specific users across multiple devices and/or virtual machines.
Monitoring and managing your end-users with CurrentWare in a Terminal Services environment works similarly. The exception is that in a Terminal Server/Terminal Services environment the server will be registered as an individual endpoint; when you run a report from PC mode it will give you a report on all the users’ profiles in a single report.
For monitoring RDP sessions CurrentWare meets your company’s monitoring and auditing needs for Windows desktop and Windows Server by tracking both local and RDP user sessions on all endpoints.
The CurrentWare Suite provides dozens of remote desktop activity reports for auditing how end-users interact with endpoint devices.
These reports include
- User logon session duration
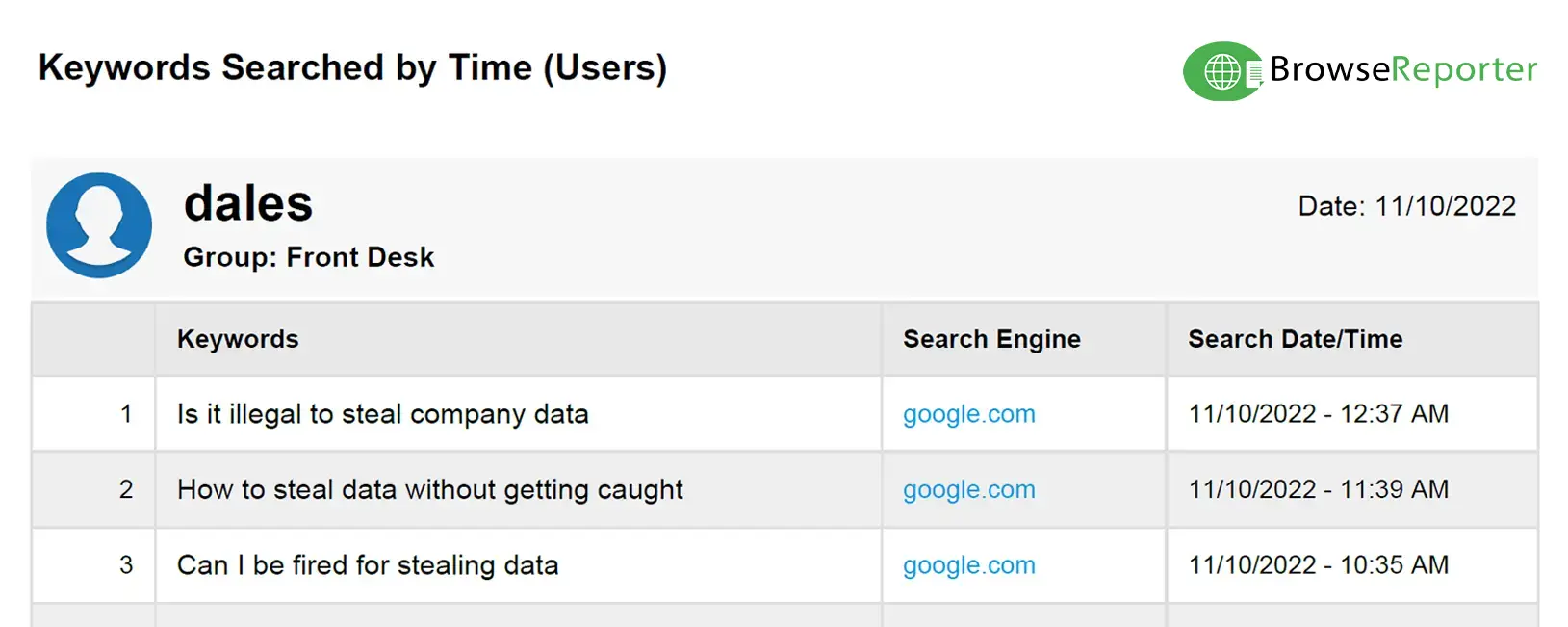
- Internet activity reports (search queries, bandwidth consumption, sites visited, browsing time)
- Application usage reports
- Active vs idle time tracking
- USB file operations reports (files copied/created/deleted/renamed to portable storage)
Many of these reports can be configured as alerts to notify you when specific actions occur on monitored endpoints.
In addition to remote user activity reports, the CurrentWare Suite includes solutions for peripheral device control, web content filtering, and remote PC power management
Track Remote Employee Work Hours (Audit Logon Events)
Tracking user activity on a daily and weekly basis allows you to correlate time spent working remotely with the hours that employees self-report.
Using enPowerManager’s User Logon History report you can audit logon events on remote computers.
This report shows you
- The user that logged in (local or domain)
- Which users connected to a certain server or computer and when
- Their logon time and date
- Their logoff time and date
- The duration of their logon session (logon-logoff time)
enPowerManager also includes a Startup and Shutdown History report to track each time a remote user alters the power state of their computer or the computer that they remotely connect to.
This report shows you
- Startup Events
- Sleep/Shutdown Events
- Hibernate/Standby Events
Using these reports you can track how long users have been connected to their local computers, remote workstations, and/or virtual machines.
This allows you to
- Verify that employees are starting and stopping their work days at expected times.
- Audit remote connections for off-hours access (potential insider threat risk)
- Compare logon times to BrowseReporter’s computer activity reports to see how they spend their time during work hours
To prevent users from simply logging into their workstation via remote desktop, leaving for the day, and logging in at the end of the workday, you can track idle time with BrowseReporter. BrowseReporter’s time tracking features will show you whether the employee was actively using their computer during the day.
Remote Employee Productivity
Using BrowseReporter’s user activity reports you can monitor RDP sessions of your employees to track their productivity levels. BrowseReporter audits the internet and application usage of users that connect to remote computers using remote desktop and similar technologies.
If you have employees who work from home you can use the activity reports to verify that they were productive during work hours.
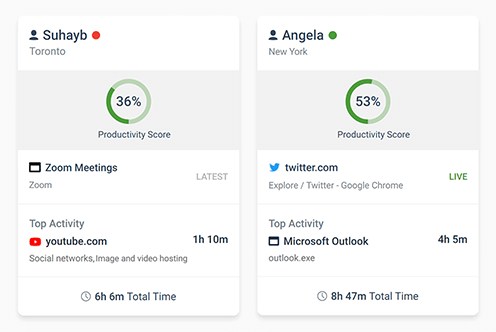
BrowseReporter even includes a pre-built employee productivity report that provides a high-level overview of how much time your remote employees spend on websites that are productive, unproductive, or neutral. These classifications can be customized to match what is considered productive for your employees.
You can even use the productivity by location report to compare productivity levels between time spent in-office vs time spent working remotely. This report tracks how much time was spent working from IP addresses that are associated with your local network and how much time was spent working from other IP addresses.
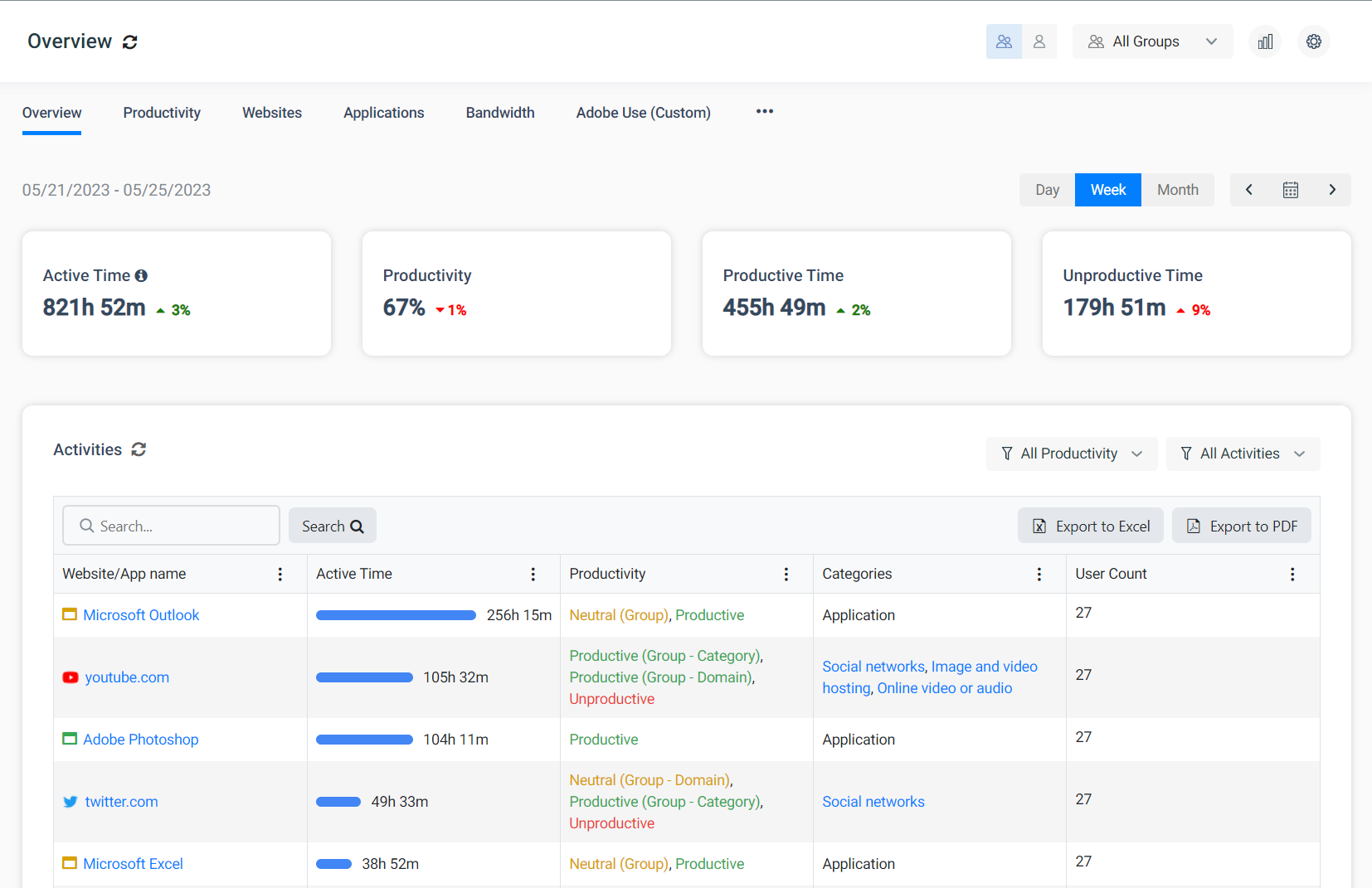
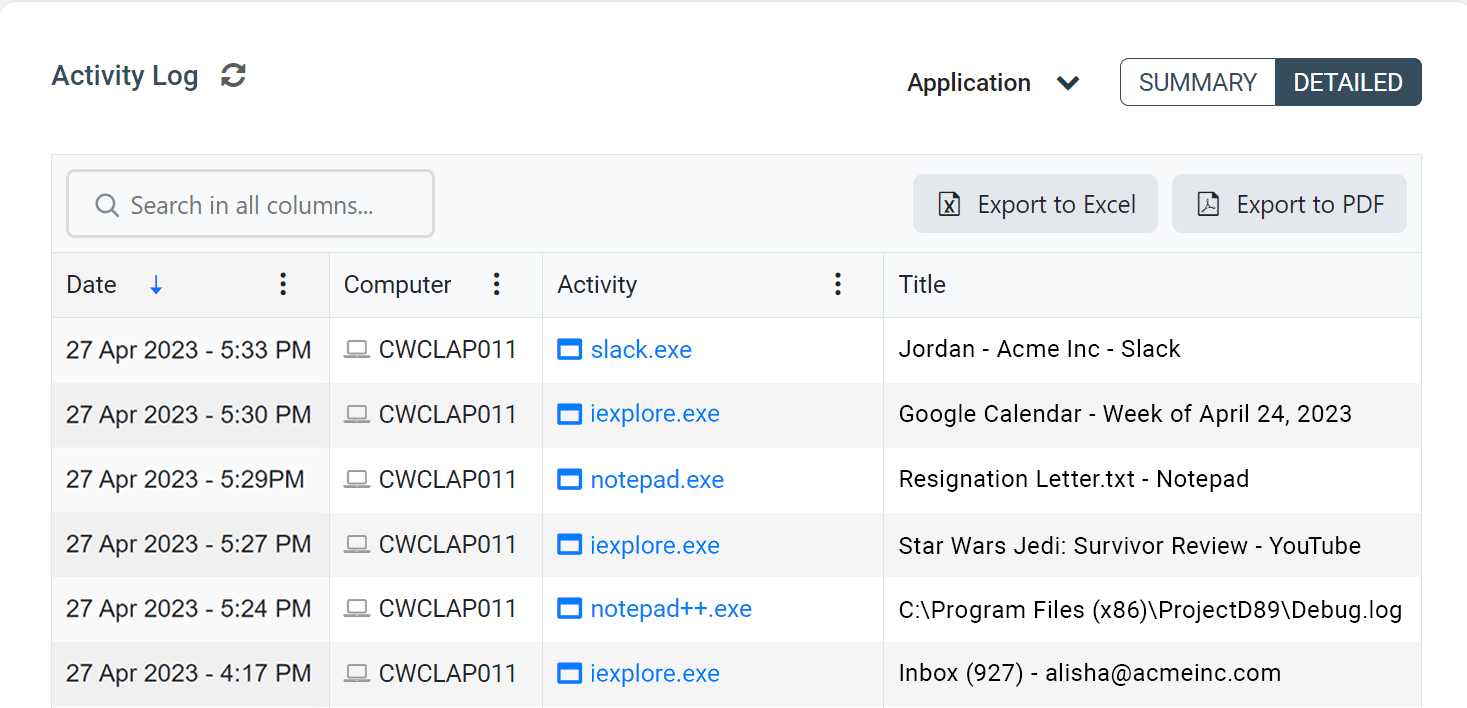
Internet and Application Usage
Monitoring internet and application usage is essential for ensuring that your remote users are in compliance with acceptable use policies.
When your remote users browse the internet or use Windows applications, their activity data will be collected by the CurrentWare client.
Samples of BrowseReporter’s computer activity reports
Bandwidth Consumption
Reducing bandwidth consumption is critical if you have several remote users connecting to your network over a VPN. Excessive bandwidth use will severely impact latency and reduce the reliability of the remote session.
BrowseReporter’s bandwidth usage reports identify the websites that consume the most bandwidth. If unproductive websites are becoming a bandwidth hog in your network you can use BrowseControl’s web filtering features to block them.
Active vs Idle Time
BrowseReporter measures the Idle Time of remote users to see how long they are away from their computers. Using the email alerts feature you can get notified when an employee is away from their computer for a predetermined period of time.
The distinction between Active Time and Idle Time is based on the end-user’s mouse and keyboard activity. When there is no input from their mouse or keyboard for a designated period of time, BrowseReporter will shift tracking from Active Time to Idle Time.
By default, the amount of time that the end-user must be inactive before BrowseReporter switches from Active Time to Idle Time is 20 minutes. This threshold can be customized to better suit your environment.
BrowseReporter’s integrated system idle time tracker sorts remote user activity into three categories based on their usage:
- Active Time is how long the employee was actively using their computer. A computer is considered active when mouse and keyboard inputs are detected.
- Idle Time is how long a given website was left open but was not actively being used.
- Total Time is the full length of time that a given websites was open (active time + idle time)
Also Read: Employee Idle Time Tracking & Work Monitoring Software
Audit File Transfers to Portable Storage Devices
With AccessPatrol’s device control features you can prevent data exfiltration when employees work from home.
With the CurrentWare Client installed on the devices you would like to monitor you can detect when USB devices are plugged into domain controllers, servers, or workstations.
You can also configure alerts that notify you when files are transferred to portable storage devices or when certain peripheral devices are inserted into monitored endpoints.
Sample USB Device Reports
File Operations
Allowed vs Denied USB Devices History
How Remote Desktop Monitoring Software Works
CurrentWare’s remote desktop monitoring software is supported on local or cloud based desktop computers, virtual machines (VMs) and servers running the Windows operating system.
So long as the underlying operating system is a version of Windows that is supported by CurrentWare, your remote users can be monitored.
This means that you can audit user activity on Desktop as a Service (DaaS) providers such as Amazon Workspaces and Citrix, self-hosted Virtual Desktop Infrastructure (VDI), or standard endpoints that are being accessed through remote desktop, DirectAccess, or a VPN.
All CurrentWare components are compatible with Remote Desktop Services (RDS) or Terminal Servers (TS). If you have users remotely connecting to a terminal server or a Remote Desktop service, you can use CurrentWare’s remote desktop monitoring software to control and track their computer activity.
Learn more about monitoring user activity in Citrix with CurrentWare
CurrentWare is known to be compatible with the following virtual machines:
- VMware
- Parallels
- VirtualBox
- Oracle VM
- Virtual-PC
- Hyper-V
Remote Monitoring Software Agent
CurrentWare’s remote desktop monitoring software tracks the computer activity of remote users using a software agent that is installed on each endpoint that you would like to monitor. The CurrentWare client agent is responsible for receiving the policies from your CurrentWare server and triggering them locally on the remote computer.
The client agent is able to differentiate between each user that is logged into the remote desktop servers. This allows you to apply unique security policies for different groups of endpoints or users. You can separate your users/endpoints into logical groupings and run reports on their computer activities.
- Integrity: The Windows user activity monitoring software offered by CurrentWare is protected from any end-user attempts to stop or uninstall the agent.
- Connectivity: The CurrentWare Suite includes continuous Windows desktop and Windows Server employee monitoring software. Even if the connection to the CurrentWare Server is temporarily lost, the CurrentWare Client will continue to monitor the user’s during their RDP and local sessions. The user activity data will be stored locally until a connection to the server is re-established.
- Visibility: The CurrentWare Client can be deployed in stealth mode or with optional privacy-enhancing features enabled.
Monitoring Local vs Remote Devices
How you will deploy CurrentWare’s remote desktop monitoring software depends entirely on the needs of your environment.
If you would like to monitor the desktops that the end-users remotely connect to, you will install the CurrentWare client on that endpoint/virtual machine, or use terminal services to provide the remote employee with a desktop that has the CurrentWare client installed.
If you would like to remotely monitor the end-user’s computer, you will need to install the CurrentWare Client on their computer. To reduce potential privacy concerns the best practice is to provide the remote user with a company-owned device and have them sign a written notice that alerts them of the monitoring.
Remote Desktop Monitoring Software FAQ
1) Can Remote Desktop (RDP) Be Monitored?
Yes. Using CurrentWare’s remote desktop monitoring software you can monitor the computer activities of your end-users. This includes logon/logoff events, internet history, and application usage. Alongside monitoring remote desktop protocol (RDP) sessions the monitoring software can also track activities on local sessions.
2) How Do I Monitor Remote Desktop Activity?
You can start monitoring remote desktop activity by downloading a free trial of CurrentWare’s remote desktop monitoring software and following these installation instructions.
3) How Do I Monitor Remote Users?
Remote users can be monitored with a few different methods
- Installing monitoring software on a computer or virtual desktop that they remotely connect to over VPN, RDP, or other remote access method.
- Installing monitoring software on the workstation that they use to work from home
So long as the monitoring software agent is installed on the device you would like to monitor and the agent has a connection to a database, you can monitor your remote users.
The types of data that you collect when monitoring remote users depends on the remote employee monitoring software that you use. CurrentWare’s monitoring software solutions allow you to track websites visited, applications used, productivity levels, logon/logoff times, and more.
4) Does CurrentWare’s Remote Desktop Monitoring Software Support Citrix?
Yes, CurrentWare is supported on Citrix. You can install the CurrentWare Clients on your Citrix Workspace so long as they are running compatible versions of Windows. | Learn More
Also Read: The 5 Best Employee Monitoring Software for 2025
Get My Free Trial
Ready to start monitoring remote desktop sessions? Get started today with a FREE trial of CurrentWare’s remote desktop monitoring software solutions.
Need help getting started? Our technical support team is here to assist you through your evaluation over phone, live chat, or email.