🆕AccessPatrol Dashboards & BrowseReporter Idle Time Alerts (v7.0)

CurrentWare version 7.0 is here! Here are the most exciting features that we’d love to highlight.
- Data Dashboards for AccessPatrol—Easily review file operations, USB device usage, and file transfers to portable storage devices of your entire workforce from the convenience of the Web Console.
- Block Bluetooth, Allow Bluetooth Audio—In AccessPatrol 7.0 you can now allow Bluetooth audio devices while blocking all other Bluetooth peripherals
- Idle Time Alerts for BrowseReporter—Get optional alerts when a computer has been inactive for a set period of time
- Quality of Life Improvements—New operator permissions, improved desktop screenshot performance, misc optimizations & bug fixes
CurrentWare 7.0 is fully compatible with Windows 11 and previous versions of Windows. See our system requirements for full details.
Learn more about updates to CurrentWare in the release notes
Data Dashboards for AccessPatrol
AccessPatrol’s USB activity dashboards work in tandem with its reports and alerts to give you the insights you need to enforce your removable media policy.
Similar to the ones in BrowseReporter, these Web Console exclusive dashboards provide a convenient overview of your entire workforce or specific groups/users—all from the convenience of a web browser.
- Get an instant overview of USB file operations and device activities
- Discover peaks in device usage and attempts to use blocked devices
- See the most common portable storage devices and file types
Once you’ve updated to version 7.0 you can find the new dashboards by clicking on AccessPatrol; you will be taken directly to the dashboard. If you’d like to access AccessPatrol’s other options you can select “Manage” under AccessPatrol in the left-hand navigation pane.
What AccessPatrol Tracks
At this time, AccessPatrol can track activities from the following peripherals:
- Portable storage devices such as USB flash drives, external hard drives, optical discs, tape drives, and SD cards
- and Mobile devices including smartphones, PDAs, and tablets
This device usage data is used to populate various graphs across AccessPatrol’s dashboards. You can further refine how granular this data is by limiting the time frame, selecting only specific groups, and even investigating individual users.
Having these metrics available at a glance makes detecting potential insider threats far more efficient as your organization scales.
Any groups or users that need to be reviewed further can be investigated using the more granular dashboards and AccessPatrol’s device activity reports.
For a more proactive approach to insider threat management you can set up targeted alerts that will notify designated staff members when these high-risk activities occur.
For the most up-to-date information on AccessPatrol’s activity tracking and data loss prevention capabilities, visit our knowledge base or the AccessPatrol product page.
Overview Dashboard
In the overview dashboard you can review the following metrics:
- File Operations that happened over the selected time period, including the number of files that have been copied/created, the number of files that have been deleted, and the number of files that have been renamed/saved as.
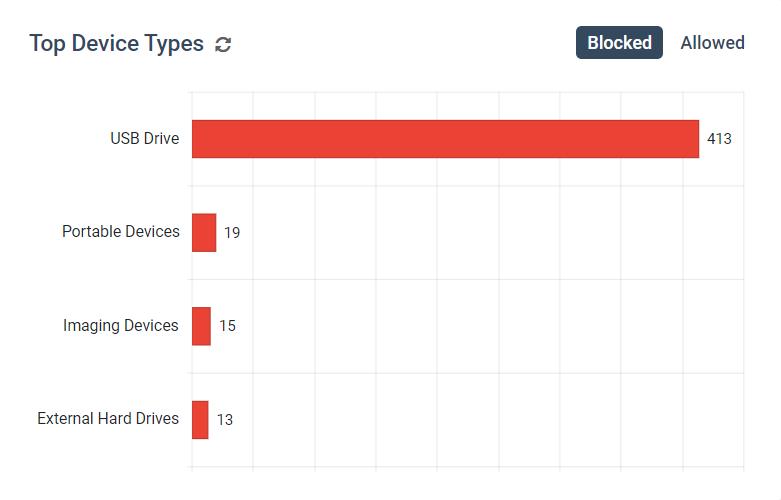
- Overall Device Activities, with a breakdown of how many of the peripherals were authorized and how many were blocked from use.
- The Top 5 File Types graph shows the most common file types that are copied/created or deleted to and from portable storage devices
- The Top 5 Device Types graph shows the most common classes of peripheral devices that are blocked and allowed
- The Top 5 Files Operations graph shows which groups or users have the greatest number of files that have been Copied/Created and Deleted to and from portable storage devices
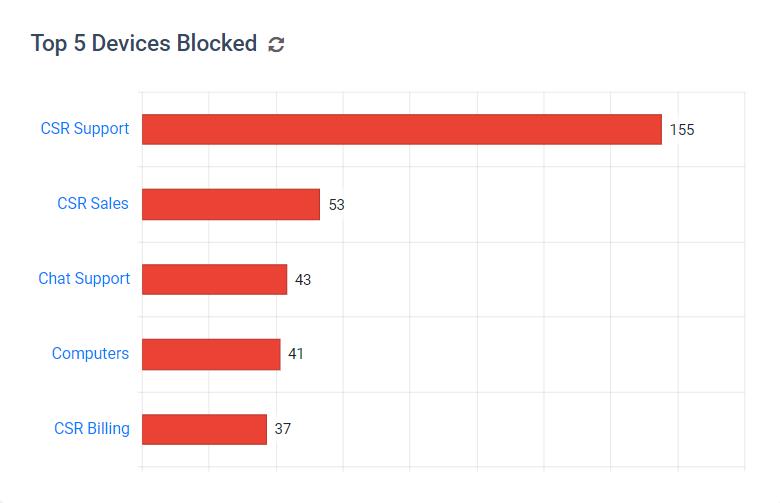
- The Top 5 Devices Activities graph shows which groups or users have the greatest number of Blocked and Allowed devices.
- And finally, The Activity Log provides access to the raw data, with controls to show and hide certain columns, filter and sort data, conduct searches, and export the data to an Excel spreadsheet or PDF. Each dashboard has their own Activity Log with columns that are relevant to that specific dashboard.
Files Dashboard
Moving on to the Files Dashboard you will see…
- A timeline of file operations that shows the relationship between the various operations over the course of the selected time period. This can be used to search for patterns in anomalous device usage, such as peaks in file transfers outside of regular operating hours.
- You will also see graphs with the Top File Types Copied/Created to internal hard drives and external devices
- Below that, we have graphs that show the users or groups that have Copied/Created or Deleted the most files
- And, just like the overview dashboard, there is an Activity Log with the raw data.
Devices Dashboard
Finally, we have the Devices Dashboard.
In this dashboard, we have…
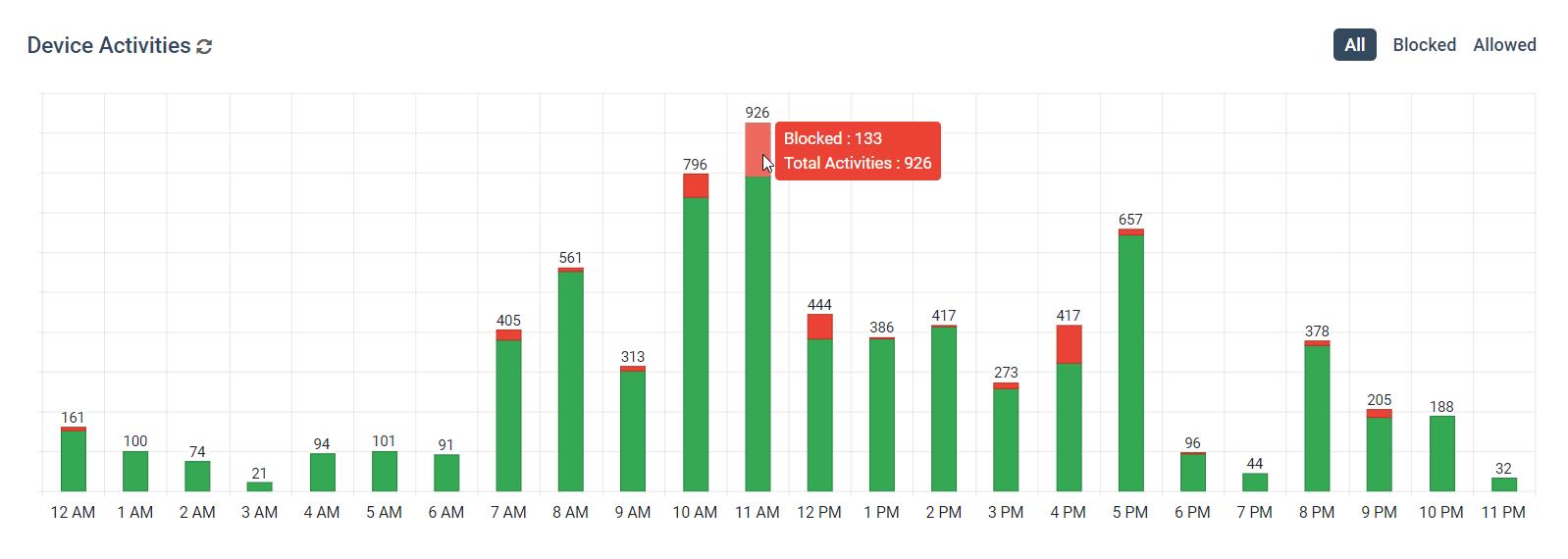
- A device activities graph that shows a timeline with the number of allowed and blocked devices each day. This can be further refined to show an hourly breakdown of a specific day so you can find out what time your users were attempting to use blocked devices.
- Next, we have graphs with the users or groups that have the most allowed and blocked devices activity over the selected time period.
- An Activity Log with sorting controls to make reviewing the raw data easier
AccessPatrol Use Case Demo: Investigating Insider Threats
As you can see in the screenshot above, we have a user that is repeatedly trying to use devices that have not been approved for use by the organization.
While this could just be an accidental oversight on the user’s part, there’s a risk that it’s something much more serious.
For example, what if this is actually a disgruntled employee trying to steal trade secrets or sensitive customer data so they can bring it to a competitor, or worse, sell it to cybercriminals on the dark web.
Between the costs associated with a damaged reputation, fines, loss of competitive advantage, and remediation, a data breach like this could completely ruin a company.
Before we confront this employee or send them for retraining, let’s investigate this incident further so we can make an informed decision.
Since AccessPatrol is currently blocking any devices that are not explicitly allowed, I know that the only way sensitive data is leaving through a USB drive is if it’s a device that we’ve allowed before.
With the Activity Log we can use the filters, sorting, and column options to isolate our view to the entries we’re the most interested in.
Once we find something that looks off, we have more than enough information to confront this employee and take any necessary corrective actions.
Block Bluetooth Except for Bluetooth Audio Devices (AccessPatrol)
In previous versions of AccessPatrol Bluetooth devices could only be set to Full Access or No Access. In version 7.0 we’ve introduced the option to allow Bluetooth audio devices while restricting other Bluetooth devices.
To do this all you need to do is:
- Open AccessPatrol
- Click on Device Permissions
- At the top of the window under “Device Permissions for“, select the group of computers or users you would like to restrict
- Under Wireless Devices > Bluetooth, click “Full Access”
- Change Bluetooth from “Full Access” to “Allow Audio Only”
- Click Apply to save your changes
As with many of our other features, this update was introduced thanks to the valuable feedback of our customers. If you have features you’d like to see in a future release you can get in touch with us on our contact page.
Idle Time Alerts for BrowseReporter
With BrowseReporter’s new employee PC idle time alerts, you can get optional email alerts when a computer has been inactive for a set period of time.
Parameters you can control in v7.0:
- Alert name
- Email addresses the alerts will be sent to
- Idle Trigger: How many minutes the computer needs to be idle before an alert is sent
- The computers you’d like the alert to apply to
- Working Days: Select the days you’d like the alert to apply to
- Start/End Time: Select the timeframe you’d like the alert to apply to
- Limit alerts to only send one idle time alert per user per day
Learn More: How to Set Up Email Alerts in BrowseReporter
Quality of Life Updates
- New User Operator Permissions—CurrentWare allows you to add trusted Operators and limit the settings they can adjust and the data they can see. In version 7.0 we’ve added further controls for Operators in the User role.
- Improved Desktop Screenshot Performance—We’ve made several backend adjustments to optimize the performance of BrowseReporter’s desktop screenshot capturing feature.
- Optimizations & Bug Fixes—The CurrentWare team is committed to providing an easy-to-use and high quality product. In each release we dedicate time to optimizing the performance and usability of our solutions.
Conclusion
CurrentWare version 7.0 is available now. To get access to the latest features, you will need to update your CurrentWare deployment. If you’re new to CurrentWare you can get started today with a free 14-day trial of the latest version.
See More CurrentWare Product Updates:
- Improved Reporting, AD Security Groups, Category Descriptions, and More! (v10.0.2)
- UI/UX Updates, Performance Enhancements, QoL Improvements (v10)
- Live Screen Monitoring, Audit Logins, DLP Upgrades, and More! (v9.0.2)
- USB Access Codes, Security Enhancements, and More! (v9.0.1)
- Full Historical Release Notes