What Is Time Theft? Are Your Employees Stealing Time at Work?

Whether through maliciousness or negligence, time theft at work is a pervasive practice among salaried and hourly employees alike.
A Forbes article has even stated that the average employee steals approximately 4.5 hours per week from their employer, totaling nearly 6 full work weeks per year. This costs businesses hundreds of billions of dollars a year worldwide.
This article will help employers and managers understand the causes of employee time theft at work, the types of time theft, and how to optimize employee time for the company’s benefit.
Software to Spot & Prevent Employee Time Theft
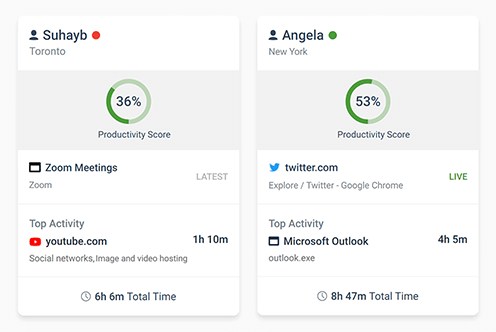
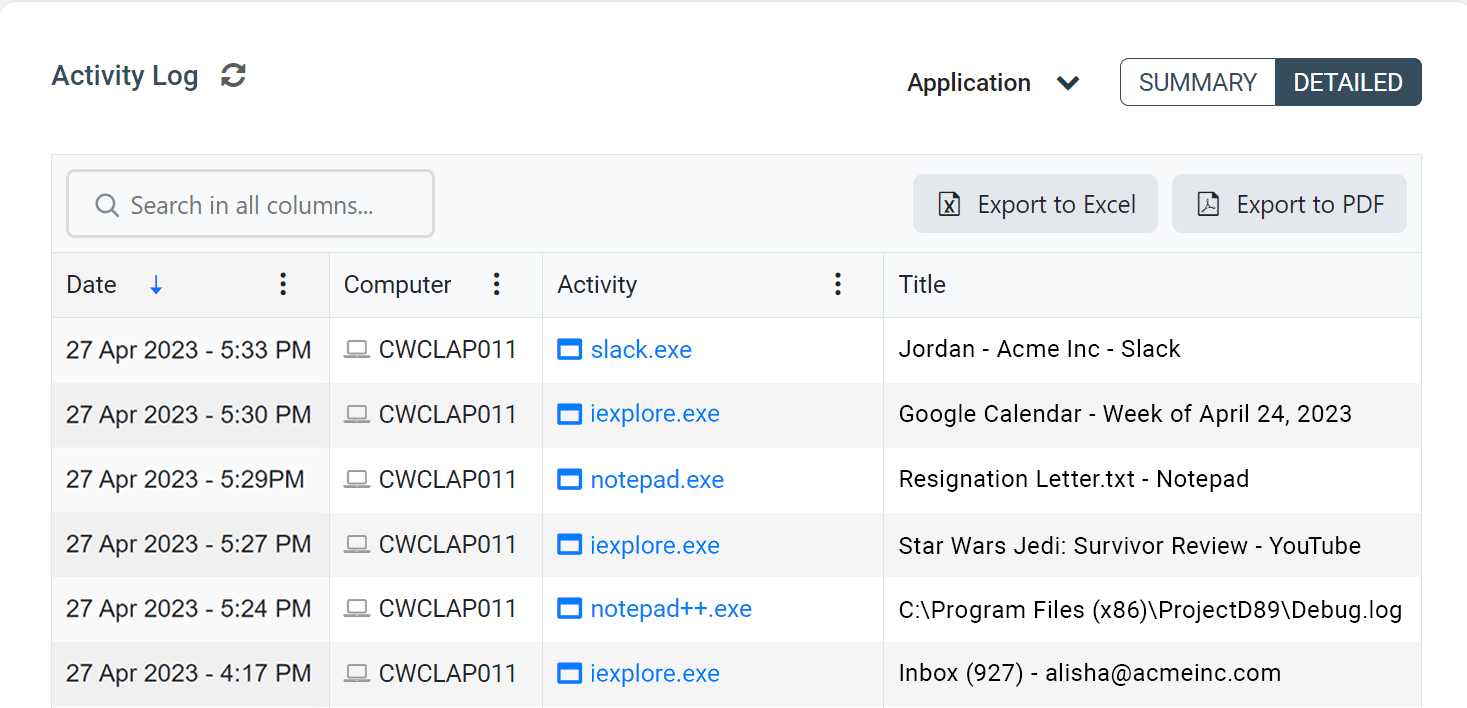
Want to ensure that your employees are focused on their tasks? With CurrentWare’s employee computer monitoring software, preventing time theft at work is as easy as installing the solution on your employee’s computers, blocking distracting websites, and running reports on their computer activity from a convenient central console.
- Track web browsing including time spent on each site, the exact URL, the web page title, and more
- Monitor application usage to see who is playing games or using unauthorized software
- Track idle time to see how active your employees are on their computers
- Monitor bandwidth usage to see who is slowing down the network with Netflix, Twitch, and Sports streaming
What is Time Theft?
At its core, time theft occurs when an employee accepts payment for work or time they did not actually complete. This practice comes in a range of severity, from employees mismanaging their allocated break times all the way up to intentionally fraudulent claims.
This practice is not always done maliciously, as is the case when employees accidentally forget to punch in/out on their time cards or if a lack of employee time tracking infrastructure causes them to overestimate time spent on work or underestimate time spent on breaks.
This theft of time goes both ways, too. A 2018 report from Good Jobs First and the Jobs With Justice Education Fund found that many leading U.S. employers have engaged in wage theft to reduce their payroll expenses. These payroll-profiting practices include forcing employees to work off the clock or depriving them of required overtime pay.
On the employer’s side, in 2011 the American Society of Employers estimated that 20% of every dollar earned by a U.S. company is lost to time theft at work.
Types of Time Theft (How do Employees Steal Time?)
In addition to what is covered in this section, time theft at work could also include “cyberloafing” with social media and personal emails, “goofing off”, spending excessive time socializing, sleeping, playing games, working unauthorized overtime, exaggerating the time spent working on tasks, and working on personal tasks and projects at work.
Buddy Punching
“Buddy Punching” is a form of time card fraud where an employee clocks in on the behalf of another employee, allowing them to get paid for time that was not spent at work.
The American Payroll Association reported in 2017 that buddy punching costs employers $373 million annually.
Buddy punching is used by an employee to fraudulently claim that they worked hours that they were not actually present for. For example, this could range from having someone punch them in when they are running late from an allocated break to taking entire days away from work while claiming their time was spent working.
A 2017 survey conducted by PollFish found that 16% of US workers aged 18+ admitted to participating in buddy punching and time clock fraud. This high percentage of buddy punchers should be alarming to all companies, especially considering that some people surveyed would likely not even admit to committing time clock fraud themselves.
Fraudulently clocking in on a time clock may run afoul of various laws. Those that are caught stealing time by intentionally manipulating their time clock may be subject to an employee time theft punishment including and up to dismissal.
Overextending Allocated Breaks Without Permission
There are many different types of work breaks and the amount of time allotted to each can vary. The most common types include lunch, bathroom visits, smoke breaks, snacking, and general rest.
In most instances, staff members can be allotted 30 minutes to an hour for a standard lunch break. In more labor-intensive jobs, it is common practice for the boss to allow more frequent and/or longer breaks in order to prevent exhaustion.
Overall, there are many studies that promote the health benefits that come with allowing employees to take brief pauses throughout the day, including this study by Science Daily that claims employees who take a break every hour are more productive than those that don’t.
So, there’s not much of an argument against allowing pauses throughout the work day. In fact, there are laws throughout federal and local governments that mandate them. But what happens when employees start abusing the amount of time they spend on break and take longer rest periods than allowed?
Let’s do a quick extrapolation and see how it breaks down over the course of a year.
Employee X takes a 40 minute lunch instead of their allotted 30 minutes each day. Over the course of a 5 day work week, that’s 50 minutes per week that is wasted. 200 minutes over the period of a month. 2,400 minutes throughout the year.
That’s a total of 40 hours wasted annually on lunch breaks alone, the equivalent of an entire week’s worth of work. If Employee X is being paid $20/hour, then their actions costs $800 annually in lost time.
When breaks become an excuse for excessive personal time at work, your business is losing precious employee time and attendance.
Misuse of the Internet
Technology has helped practically every type of business develop its services and workforces to be more connected, convenient, and accessible. Computers, smartphones, and the internet help companies connect with customers and allow large workforces to easily collaborate on group projects.
Without the internet and its technologies, many companies would not even exist. But, despite its necessity and many benefits, the internet can be misused by employees in a way that can cause major loss for a business.
The International Data Corporation estimates that 30 to 40 percent of employee internet activity is non-work-related. This misuse of the internet in the workplace is costing US businesses $63 billion in lost productivity each year, according to Websense Inc.
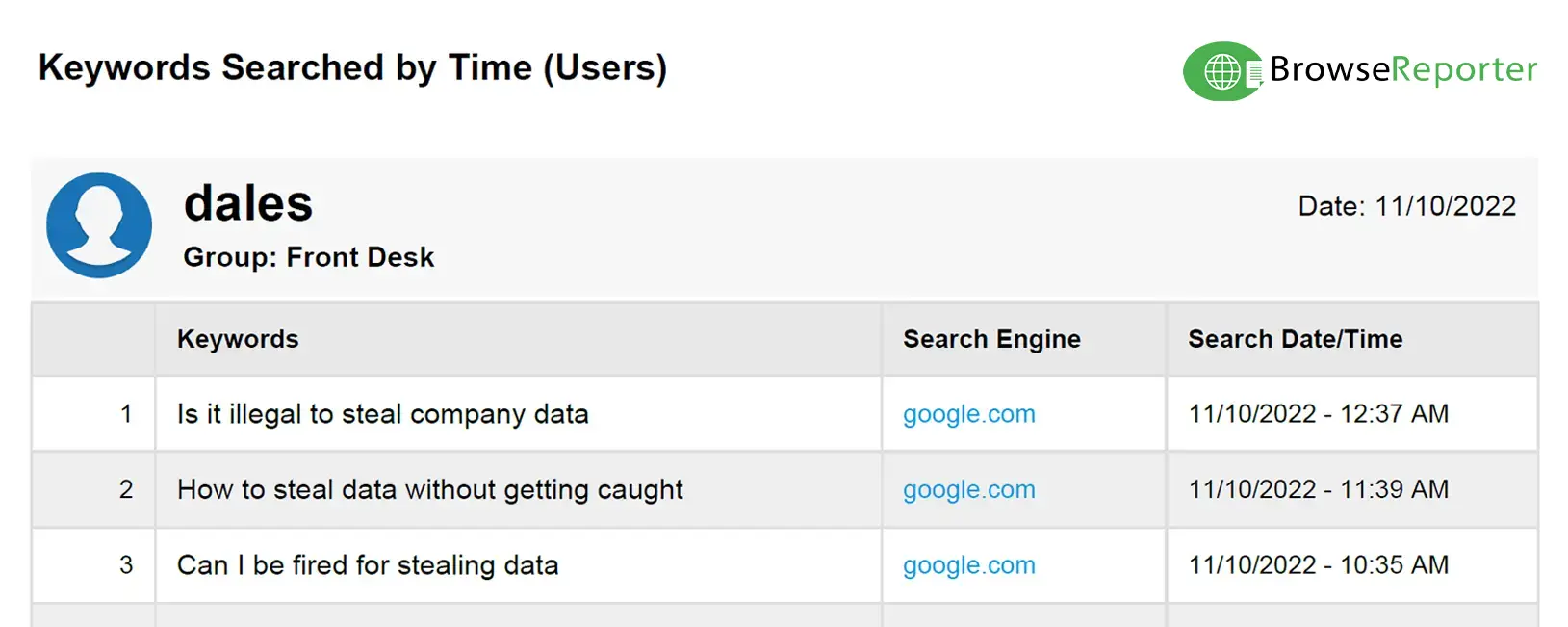
The internet has been around for decades at this point, and we all have likely witnessed an employee switching the screen on their desktop so that they don’t get caught playing games, checking their personal email, or scrolling through their social media feeds during their shift.
While it’s true that short, frequent breaks make people more productive, excessive unproductive web browsing may cause employees to lose more working hours than they realize.
Employers can use employee and computer monitoring tools to track and correct excessive cyberloafing; but what about employees who simply use their smartphones?
With smartphones in everybody’s pocket, staff members can freely check social media, stream movies, and play time-consuming games without being caught.
Smartphones make employee productivity management a difficult task:
- They’re personal devices, so you can’t monitor or restrict web browsing and app usage on them like you can on a business-provided device.
- Even if the office network’s WiFi is filtered and monitored, staff members can readily use their personal data plans to surf the web.
- Even with surveillance cameras in place, staff members can just take their phones to an area without video surveillance.
However, unless you work in an industry with above-average security requirements (such as national defense and other highly classified government environments), outright banning cell phones isn’t the right way to go.
Banning cell phones in the workplace for productivity reasons could harm morale by communicating to employees that they are not trusted to self-manage their own workloads. As a best practice, you should focus less on the individual ebbs and flows of concentration and more on the quality and timeliness of the employee’s output.
Paid Leave Fraud
One of the more extreme and legally technical forms of time theft occurs when employees abuse their organization’s paid leave program.
Whether it be for new parents, or for those who are battling a chronic or debilitating illness, paid leave is common within most companies and is often backed by government policy and programs.
Unfortunately, the steps that are involved in permitting a paid leave for an employee can be extensive, and there have been many cases in which the employee was abusing their paid leave.
In Ottawa, Canada, a city employee was found to have taken a total of 32 annual leave days over a number of years without ever recording it into the time tracking system.
Another employee from the same municipal workforce was found to have been handing in medical notes in order to claim paid time off while actually working for a different business during those paid leave days.
When paid leave is granted, it is the organization itself that needs to pay the employee during their leave. Fraudulent abuse of the paid leave system causes significant business losses.
Why Does Time Theft Happen?
Employee Burnout
Employees are more likely to commit time theft at work when they are burnt out. Chronic stress, a toxic workplace culture, and a lack of equity in the workplace are all potential triggers for burnout in employees. Employees that become burnt out will be actively disengaged and far more likely to commit time theft as a way of getting back at their employers.
Employees that do not feel fairly compensated for their efforts or are otherwise dissatisfied with their work-life are less engaged and are more likely to exhibit counterproductive work behaviors (CWB) such as a lack of engagement, excessive personal activities during work hours, or fraudulently reporting hours worked.
Financial Troubles
Employees that are experiencing financial distress are more likely to steal time from their employer. They may manipulate their time card to misrepresent the time they spend on the job site in order to be paid for work that they did not put in.
Stealing time in this way may also provide a window of opportunity for the employee to work a second job for a few hours per week while claiming that time on their primary employer’s time clocks. This payroll manipulation allows those in financial distress to illegitimately claim more hours on their payroll.
Poor Supervision
One of the most prevalent causes of time theft at work is quite simply poor on-site supervision. When unscrupulous employees know that they can get away with stealing business time by playing games, taking extended breaks throughout their shift, making excessive personal phone calls, and browsing the internet while on the clock they could be incentivized to do so.
While managers should not be micromanaging all of the time their staff spends at work, there needs a culture of accountability in place to avoid payroll manipulation and disengagement. One employee accidentally running late from their 60-minute lunch break may be no big deal but employers need to be willing to perform corrective actions to prevent intentional types of time theft.
Tools such as scheduling software help improve employee supervision with insights into how employees are allocated and how they are expected to spend their time.
Lack of Motivation
Employees that are unmotivated by their daily tasks are far more likely to waste company time and become time thieves. Whether the work is too easy or simply uninteresting, workers will often find non-work-related activities to pass time through the day.
To keep employees engaged while on the clock you should provide more rewarding tasks. Depending on the individual employee a more rewarding task could be one that is more challenging, requires more relevant skills, or involves added responsibility.
Workplace Culture
Employees that avoid work while on the clock may be influenced by their immediate colleagues and managers. For example, if low-level forms of time theft at work are prevalent and consistently left unaddressed this will create a culture that employees use as an example of what is acceptable for them to do.
Another way that company culture can contribute to supporting various types of time theft is when employees are in an environment that disproportionately punishes tardiness.
Naturally, excessive time mismanagement needs to be addressed to prevent time theft at work. That said, if a few minutes per week is punished too severely the lingering fear of punishment may incentivize an employee to consider buddy punching or other forms of punch clock manipulation rather than being transparent about their accidental 61-minute lunch break.
Lack of Clear Guidance & Accountability
Time theft can occur when employees are not given clear expectations. If employees are not aware that the less-malicious examples of time theft (excessive socializing, over-extending breaks, etc) are a concern for the organization, they may inadvertently participate in these activities without a second thought.
By clearly communicating expectations for time spent at work and enforcing those expectations through formal policies, codes of conduct, regular message reinforcement, and monitoring, you can establish a baseline with which employees can operate from and allow them to be coached to better suit the needs and expectations of your organization
On the other hand, time theft can also happen maliciously.
Sometimes employees that willingly engage in time theft may also be doing so simply because the opportunity is present. Part of an organization’s time theft mitigation strategy needs to account for this possibility by implementing systems that can accurately track and verify employee time.
Unscrupulous Employees Working From Home
A lot has happened since the COVID-19 pandemic first hit in March of 2020. One of the biggest changes to many people’s daily lives has been the shift to working from home.
With the virus’ ability to quickly spread, employers were forced into adapting work from home strategies in order to keep afloat. This meant that workers were taking their office equipment to their homes and make-shifting their own sort of office environment in order to emulate a traditional work experience.
But the fact remains that a home office is not a traditional office space, and with that comes the inevitable fact that employee supervision for remote workers is very hard to manage. Without the oversight of managers and peers, employees working from home are susceptible to a wide range of distractions. Disgruntled or unscrupulous workers may even take advantage of this lack of visibility to steal time from their employers.
These incidents can range from running personal errands during work hours, not working their agreed-upon hours, or taking extended breaks while on the clock without the support of their business. Each of these distractions costs companies money in time lost and are prime examples of remote employee time theft.
How to Prevent Time Theft at Work
Monitor and Report Time Theft at Work
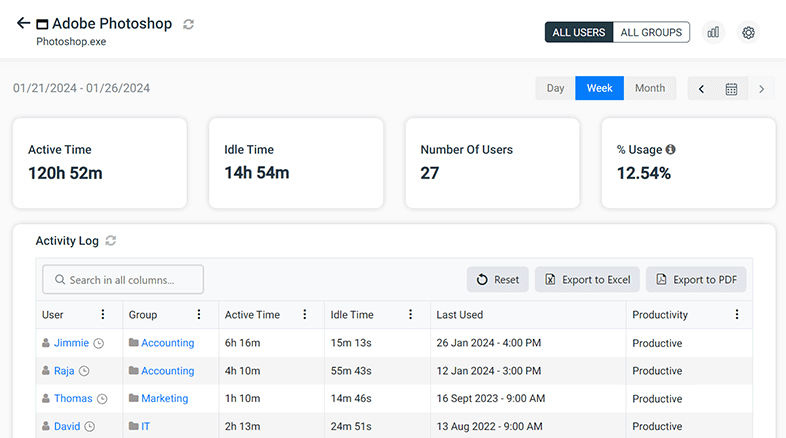
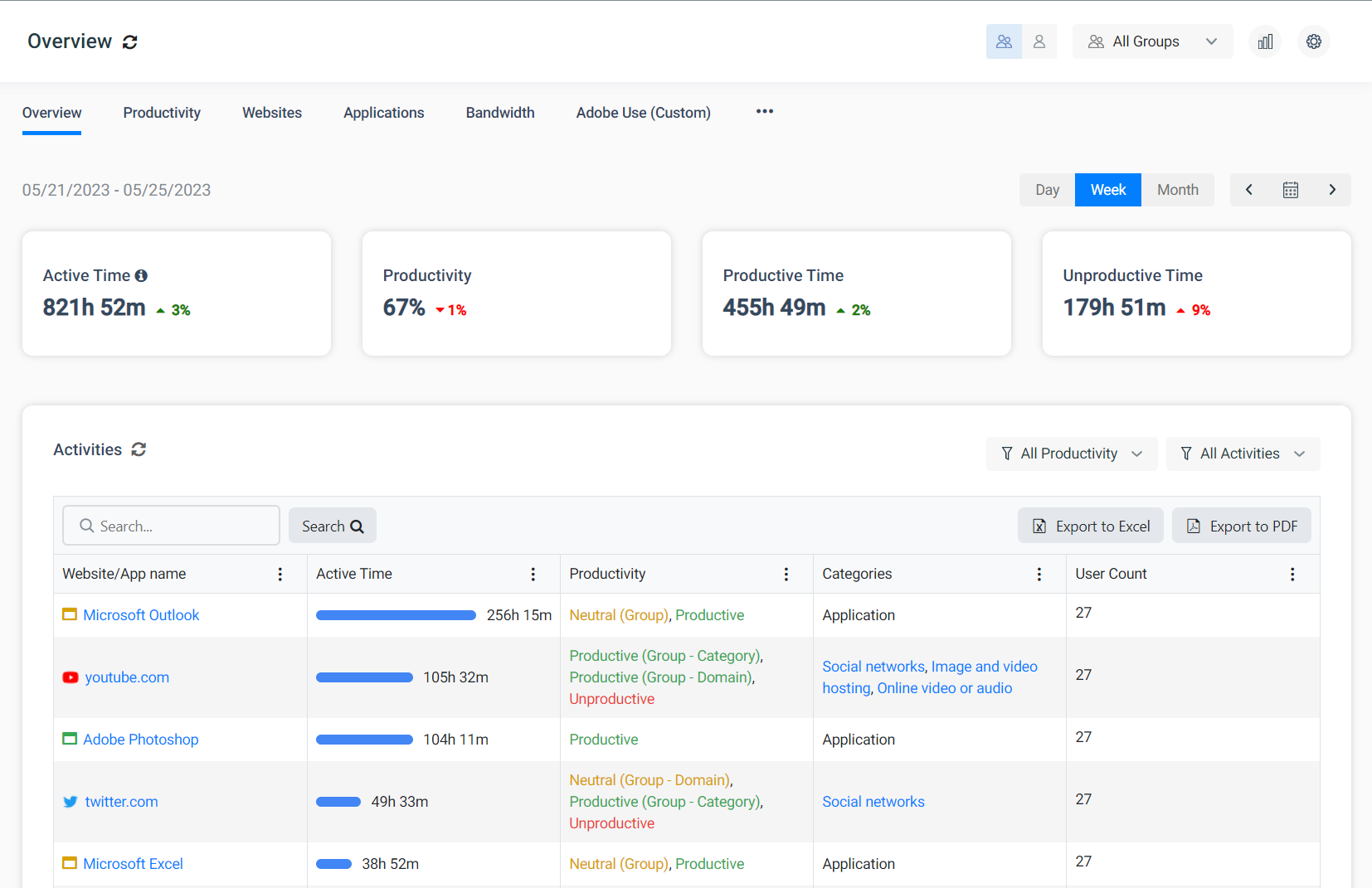
One of the most difficult parts of mitigating time theft is a lack of resources for identifying its prevalence. Software to monitor employee internet usage will give human resources (HR) and management the insights it needs to understand the prevalence of time theft in your organization.
With the data collected through employee internet monitoring software, your organization can make educated coaching decisions and improve your employee’s mindfulness of distractions they engage in and how it may be impacting their performance.
Tools for Monitoring & Preventing Time Theft
CurrentWare is a global provider of solutions for web filtering, internet usage monitoring, bandwidth tracking, and data loss prevention.
If you would like to better understand how the internet is used (or misused) in your workplace you can try our internet monitoring solution BrowseReporter and our web filter BrowseControl with a FREE no commitment 14-day trial.
BrowseReporter Computer Monitoring Software
- Track Internet Activities
- Automated Email Reports
- Bandwidth Monitoring
- Record Application Usage
- Remote Screen Capture
BrowseControl Web Filter
- Control Internet Access
- URL White / Black Lists
- Category Filtering
- Application Blocking
- Port Filtering
Secure Time Cards & Time Tracking
With a modern automated time clock or time tracking application that uses multi-factor authentication systems you can reduce the risk of buddy punching on time clocks and maintain an accurate payroll.
Time & Attendance Policy
Clear guidance and policies/codes of conduct are essential tools for establishing accountability, communicating expectations, and preventing punch clock/payroll manipulation.
Organizations need to develop time and attendance policies that are appropriate for the job at hand and easy enough for employees to understand. These policies should be regularly reviewed and administered in order to prevent employee time theft.
With your time and attendance policies set, your staff will have a pillar to be held accountable to. Ensure that they clearly understand your organization’s expectations and reinforce their accountability to those expectations through enforcement and coaching.
Block Unproductive Websites and Apps
Internet time theft is one of the most pervasive example of time theft at work. With internet time theft, employees spend excessive personal time on unproductive websites and applications. Actively disengaged employees use these types of time theft to avoid work responsibilities and misrepresent the time they spend on their tasks.
A Gallup report found that actively disengaged employees cost the U.S. $450 to $550 billion per year in lost productivity. Social media, news, and games can all become a temptation for even the best of employees, amounting to significant losses.
Organizations can prevent internet time theft with internet restriction software. These solutions proactively prevent access to distracting websites during specified working hours; solutions such as BrowseControl can even by configured to allow access to unproductive websites during designated rest periods, allowing employees to take care of personal tasks.
To prevent employees from downloading distracting applications such as games, some internet restriction tools also comes with integrated features for blocking unauthorized downloads.
Tips for Employee Monitoring & Time Tracking
One of the difficulties of employee monitoring is that employees may feel that they are not trusted to manage their own schedules or they may worry that “big brother” is micromanaging their time and making uninformed judgements about their work ethics based on the data collected.
To help generate much-needed support from the employees in your workforce, there are ways to balance your time theft strategy to a reasonable standard.
Monitoring While Respecting Privacy
If you would like to use monitoring solutions as a part of your time theft mitigation strategy, it is important to respect the privacy of your employees.
Only use the amount of monitoring that is appropriate for the needs of your organization, and ask for explicit consent from employees that will be monitored as a part of their work activities. For traveling or remote employees that require the use of a tracked device for work, it helps to provide them with a dedicated work device as the monitoring of personal devices can feel like a significant privacy violation for most employees.
Set Reasonable Expectations For Your Employees
With all of the concerns your organization may have regarding time theft it is important to consider that typically, the ultimate goal is to cultivate a workforce that is full of employees that are happy, engaged, and productive. Internet and application monitoring should be used to identify and coach repeat offenders and address productivity issues, not to micromanage your employees.
When assessing the prevalence and severity of time theft, you should consider the “human factor” behind your workforce—your workforce is full of multi-dimensional humans with needs outside of their immediate work obligations. By allowing a reasonable degree of flexibility for non-work activities such as taking personal calls/emails as needed or engaging in brief team-building conversations, you will make your staff feel trusted and valued, leading to an increase of engagement and productivity through greater job satisfaction.
Conclusion
While not all forms of time theft are malicious, having employees stealing company time is a significant drain on productivity. If left unchecked stealing time at work can become a pervasive issue. With a combination of time clock management software, company policies, web filtering and internet monitoring software, and proactive supervision you can prevent employee time theft in your company.
Ready to take back control over internet abuse in your organization? Get started today with a FREE trial of our internet monitoring and web filtering software solutions.