Software Asset Management – Why Track Employee Application Use?
Did you know that underutilized software cost businesses a staggering $34 billion per year? With a properly executed Software Asset Management (SAM) strategy you can optimize the capital efficiency of your business and avoid paying for software that your employees aren’t using.
Monitor Employee Software Usage With BrowseReporter
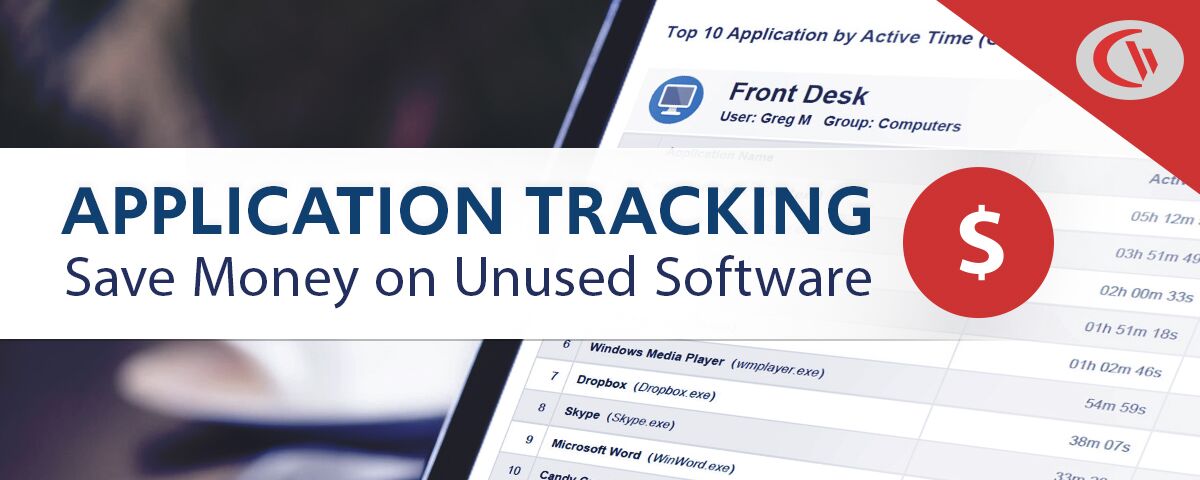
Need insights into what software is being used, how often, and who is using it? Start monitoring employee internet and app use today with a free trial of BrowseReporter, CurrentWare’s computer activity monitoring software.
BrowseReporter makes tracking software license usage possible with its easy-to-use reporting utility and dashboards. At a glance you can review the software usage of your employees, including timestamps of the applications they use each day, how frequently they use specific applications, and their most used applications.
CASE STUDY
Activity Insights in Citrix Workspace Drives Software Adoption and Productivity
What is Software Asset Management and Why is it Important?
Software Asset Management (SAM) is a subset of IT Asset Management (ITAM) that focuses on the optimization of software usage, procurement, deployment, maintenance, and disposal in an organization. SAM includes the management of software assets, product versions, licenses, and the media used to deliver the software. Aside from license cost optimization SAM also manages the lifecycle of a software product and determines the software’s function in the organization.
A subset of SAM is Software License Management (SLM), which focuses on the optimization of software licenses used within an organization. The goal of SLM is to reduce costs by reducing the amount of unused licenses, optimizing the use of existing licenses, and consolidating redundant licenses. SLM also refers to the optimization of related costs associated with customer support and product maintenance.
SLM can be further refined to Software License Compliance (SLC), which is the practice of maintaining compliance with the terms agreed to in End User License Agreements (EULA). Common terms that organizations need to maintain compliance with include ensuring that only permitted end-users are operating the software, required device configurations are maintained, and that the software is only used in permitted geographic locations.
A successful software asset management (SAM) strategy will help you understand:
- Which applications are we paying for?
- How many employees within my organization use a given software?
- Do we have enough (or too many) licenses?
- What will the total costs of this software be throughout its lifecycle?
Throughout this article we will use Software Asset Management (SAM) as an all-encompassing term for both SLM and SLC.
The Goals & Benefits of Software Asset Management
Detect & reduce shadow IT
Shadow IT – also known as Stealth IT, Client IT, or Fake IT – is any system, solution, or software that’s used by the employees of an organization without the knowledge and approval of the corporate IT department.
An effective software asset management program will include a software audit that detects all of the programs that are currently used by the organization, including those that have not been officially adopted for use in the organization.
Also Read: Software License Optimization with Cost Insights by CurrentWare
Reduce software license costs
Underutilized software cost businesses in the US and UK an estimated $34 billion per year. SAM helps organizations manage application sprawl and reduce software costs by tracking the utilization rate of applications.
By monitoring the application use of their employees, an organization can make data-informed decisions regarding the need to purchase new licenses and decommission underutilized software.
Reduce corporate risk
SAM is a critical component of corporate risk management. A failed software compliance audit can cost an organization as much as $150,000 in fines per violation. An audit can be failed due to the presence of pirated software, using more licenses than allotted, or other violations of the software’s End-User License Agreement (EULA).
These audits are more frequent than some may realize; a report from Gartner anticipated that 68 percent of enterprises get at least one audit request each year.
The Risks of Poor Software Asset Management
Compliance violations
Each software vendor has their own End-User License Agreement (software license agreement) that the organization must adhere to. Without adequate oversight, an organization runs the risk of violating its agreements with vendors.
Increased costs
- Fines & Penalties: Non-compliance fines from a failed software compliance audit (piracy, exceeding license entitlements, etc)
- Increased SaaS Spend: Software-as-a-Service (SaaS) vendors often license their software by the user. If the organization is being billed for more users than are actively using the service they will have sub-optimal operating expenses. A proper SAM strategy must include SaaS spend management as a component.
- Productivity Loss: If an insufficient amount of licenses are available for the legitimate need of the organization they will experience an increase in downtime. They may also lose billable hours to time spent procuring software for a need that is adequately met by an existing solution.
- Over Licensing: Poor software license management can cause the organization to purchase a greater volume of licenses than they legitimately need.
Lost productivity
Without meaningful insights into the application usage of their employees, an organization risks not having enough active software licenses. If all of the available licenses are already use,d they will experience significant downtime as their other employees cannot make use of the software.
Monitoring the application usage of their employees provides organizations with the historical data they need to decide if a greater number of licenses needs to be procured to meet the demands of peak usage periods.
How To Get Started With Software Asset Management
Audit Your Existing Software
To start, you need to have a thorough understanding of all of the software currently being used by your business. You will need to catalogue the existing licenses your company has, make note of ongoing software expenses, and monitor employee computer activity to determine whether or not the existing solutions are being used.
- Audit your organization’s software procurement history for existing licenses
- Monitor employee application use to determine current utilization and detect the use of undocumented software
- Monitor employee web activity for the use of SaaS platforms
- Categorize the existing software and consolidate any redundant solutions
- Make note of any upcoming renewal dates for monthly/annual subscriptions or maintenance plans
Establish a Software Procurement Process
To reduce unnecessary software expenditure in your business you will need greater control over your software procurement and decommissioning process. This can be accomplished by establishing policies and procedures surrounding the acquisition, documentation, deployment, usage and retirement of software.
Your organization should have official software procurement procedures in place that defines who is permitted to make purchases, when those purchases can be made, and what channels must be consulted for approval before a solution can be purchased and deployed. This will reduce unexpected shadow IT costs and ensure that each software purchase is evaluated against your existing capabilities before approval.
Also Read: How to Track Software License Usage With BrowseReporter
Track & Control Employee Software Use (Software Metering)
The practice of tracking and maintaining software licenses is known as software metering. The goal of software metering is to ensure that license limits are enforced and that licenses are available for each user that needs one. This practice can be further split into two major categories: passive software metering and active software metering.
Passive software metering: Application use is monitored but users are not actively denied access to the software. This provides natural user activity insights that can help determine the number of licenses needed.
Active software metering: Application use is monitored and access can be denied based on a given set of parameters. For example, an organization with a limited amount of licenses could schedule application permissions to limit the number of users that can access the software at a given time.
BrowseReporter makes tracking software utilization possible with its easy-to-use reporting utility and dashboards. At a glance, you can review the software usage of your employees, including timestamps of the applications they use each day, how frequently they use specific applications, and their most used applications.
Organizations can further reduce unauthorized software use with an application blocker. Employees that are not authorized to use a given solution can be proactively blocked from launching the program, reducing the opportunity for licenses to be activated without a legitimate need.
Ready to start monitoring and restricting software use in your company? Get started with a FREE trial.
Frequently Asked Questions
Conclusion
Sub-optimal software licensing is a significant source of capital inefficiency for many organizations. By tracking the internet and application usage of your employees you can ensure that the SaaS solutions and software products you invest in are truly necessary and used to their full potential. You can identify which products require a greater volume of licenses and which products can be decommissioned.


