What is Data Exfiltration: Threats, Techniques & How to Stop It
In 2025, data is everywhere, in your inbox, on your phone, and flowing through a maze of corporate servers. It’s the lifeblood of business, medicine, and everyday life. Unfortunately, that makes it irresistible to thieves. Not the smash‑and‑grab burglars of old but quiet intruders who watch and learn before they start siphoning off secrets. In cybersecurity circles, this quiet theft is called data exfiltration.
There’s a good reason security experts are ringing alarm bells. IBM’s 2025 Cost of a Breach report pegs the average breach cost at $4.44 million worldwide and a staggering $10.22 million in the United States. Those figures aren’t abstract – they represent ransom payments, forensic investigations, legal battles and ruined reputations
Ready to Take Control?
Stop Data Exfiltration in your Organization
- → Real-time tracking
- → Data for compliance and cost-saving decisions
What We Mean by “Exfiltration”
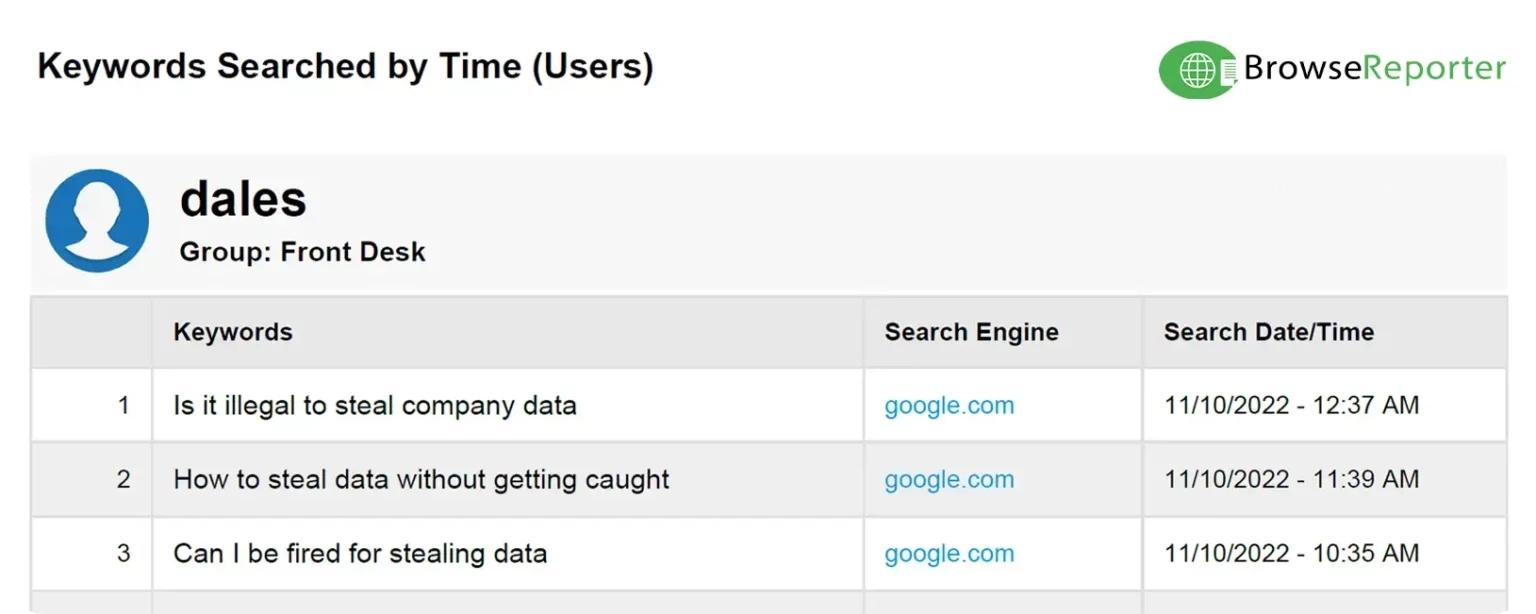
The term sounds like spy‑craft because in some cases it is. The National Institute of Standards and Technology spells it out as ‘the unauthorized transfer of information from an information system’. In plain English, someone takes data they have no right to have. That might be a disgruntled contractor copying files to a USB stick or a criminal gang that installs malware and quietly sends your customer database overseas.
This is different from leaving a confidential document on a printer or mis‑addressing an email. Those mishaps are accidents. Exfiltration is deliberate theft.
Also Read: Web Filtering Software for Business—Block Websites, Apps & More
How a Digital Heist Unfolds

Think of an attack in stages. It usually begins with scouting: attackers look for open remote‑access ports, guess passwords and even stalk employees’ social media profiles. When they find a weak point, they use it to slip inside, often with a convincing phishing email that tricks someone into clicking a malicious link.
Once inside, they search for valuable data, moving from server to server until they find it. They compress and encrypt what they want, then move it out of the network. They might send it through cloud storage accounts or hide it within legitimate web traffic to avoid raising alarms. Finally, they erase logs or alter timestamps to cover their tracks.
Security researchers at Fortinet note that phishing remains one of the most successful ways to get in. Attackers also steal data by abusing email systems or by copying files onto personal devices like phones and thumb drives. Lax cloud security is another common opening: logging into company apps from an unsecured Wi‑Fi network can give thieves a foothold.
The People Behind the Theft
Who does this? Plenty of people. Organized crime groups steal data to sell it or hold it hostage. Insiders, employees, contractors or partners, might copy files for their own gain or out of spite. And state‑sponsored hacking teams target intellectual property and government secrets for strategic advantage. Each group has different motivations, but they all rely on weak passwords, unpatched software and inattentive staff.
Also Read: Data Loss Prevention Software—Endpoint DLP Solutions
The Damage They Cause

Making It Harder for Them
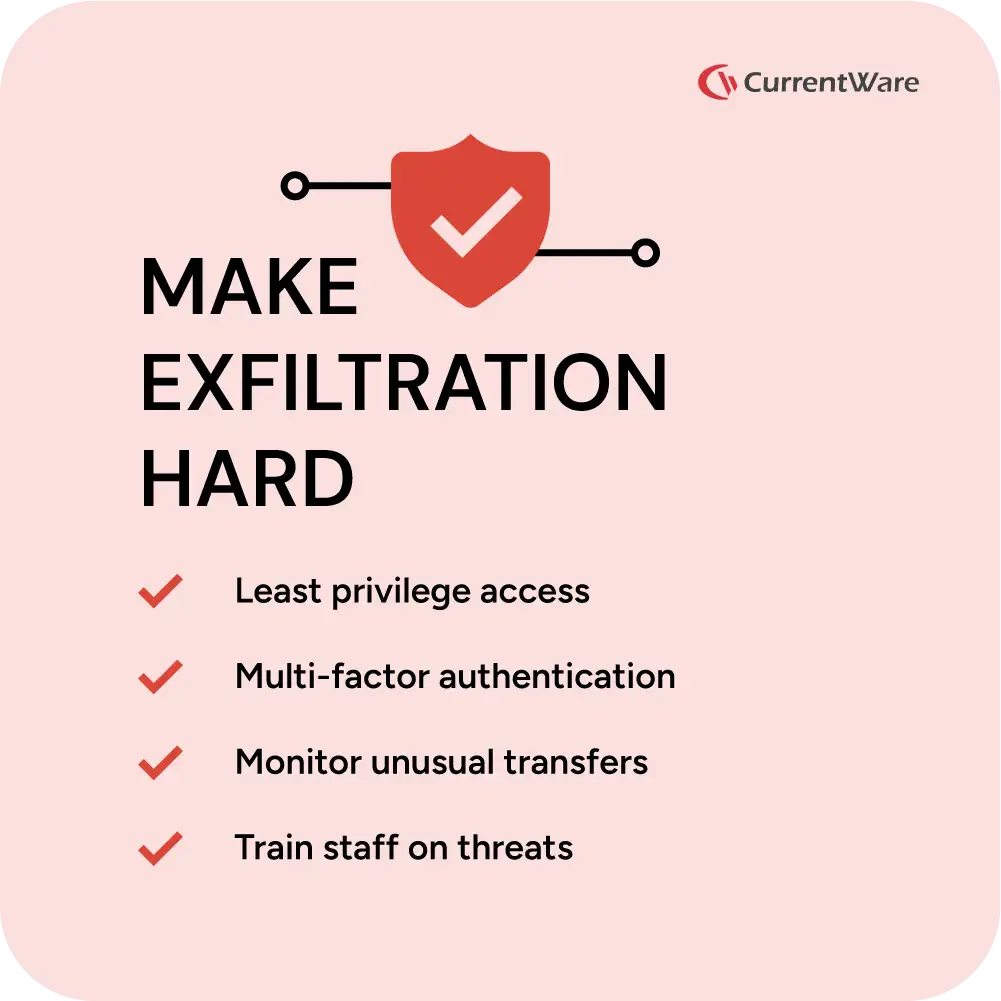
There’s no magic product that stops every attack. The best approach is to layer defenses and make yourself a hard target:
Restrict who sees what. Only give staff the access they need. If a marketing intern doesn’t have access to the payroll system, stolen credentials won’t open that door.
• Watch where your data goes. Modern monitoring tools flag unusual uploads or downloads. Some, like the CurrentWare suite, block unapproved USB drives and track file transfers for early warning.
• Teach everyone to spot traps. Even the best security software can’t protect you if someone clicks a dodgy link. Regular training helps staff recognize and report phony emails and social‑engineering attempts
• Secure every connection. Use strong passwords, multifactor authentication, and encrypted connections. Don’t let employees log in over untrusted Wi‑Fi with sensitive data.
• Know your plan. If a breach happens, you need to know who isolates the affected machines, who calls the lawyer, and who tells customers and regulators. Decide now, not during a crisis.
Also Read: Employee Internet Management Software - Monitor & Restrict Internet Use
Some Quick Answers
Is a data breach the same as exfiltration? No. A breach covers any unauthorized access. Exfiltration is the specific act of stealing data.
How do I stop employees from taking data? Limit their access, watch for unusual activity, and create a culture of security. If staff understand the risks and feel comfortable reporting concerns, you’re less likely to be blindsided.
What methods are most common? Phishing emails, misuse of company email systems, copying to removable drives and poorly secured cloud apps. Attackers disguise stolen data as regular traffic to slip past detection.
What do I do if it happens to me? Disconnect affected systems to stop the bleed. Save logs and system images for investigators. Assess what was taken and notify the relevant authorities and anyone whose data was exposed.
Also Read: CurrentWare Suite—PC Monitoring, DLP & Web Filtering Software
Why This Matters
Data exfiltration is a modern form of burglary. The thieves don’t wear masks or break windows, but their crimes are just as damaging. Understanding how they operate and taking sensible precautions can spare you from the fallout. As our lives continue to move online, staying vigilant isn’t just good practice, it’s a necessity.



