What is Endpoint Security? What is an Endpoint?

What is endpoint security, and why is it important for your company? This article will answer common questions about protecting endpoints and provide insights into endpoint security’s role in safeguarding sensitive data against malicious attackers as part of a multi-layered defense strategy.
What is the definition of endpoint security?

Endpoint security is the practice of protecting endpoint devices against a variety of cybersecurity threats. The intention of endpoint security is to safeguard sensitive data and networks against malicious attacks from threat actors such as black hat (malicious) hackers, hacktivists, state-sponsored actors, cybercriminals, and insider threats.
This is accomplished in part by improving the security of endpoint devices, though other elements of security such as network security, physical security, and cloud security also play a part in protecting sensitive data.
For more definitions related to endpoint security, check out this glossary from Solutions Review.
What is considered an endpoint device?

Traditionally, an endpoint device was any device that was literally at the end of a physical network such as modems, switches, bridges, workstations, and hubs. In modern times the addition of new devices and the widespread use of cloud architecture has expanded what we consider to be an endpoint to include any device that operates outside of the corporate firewall.
Examples of endpoint devices:
- Internet-of-Things (IoT) devices and smart devices such as watches, fitness trackers, and sensors
- Industrial Internet-of-Things (IIoT) systems such as Supervisory Control and Data Acquisition systems (SCADA) and Programmable Logic Controllers (PLC)
- Mobile devices such as laptops, tablets and smartphones
- Networking hardware such as modems, switches, bridges, servers and hubs
- Output devices such as printers
- Automated Teller Machines (ATM)
- Self-driving vehicles
- Medical devices
- Mobile kiosks
This list is far from comprehensive; as technology continues to advance we will see more and more devices becoming interconnected and contributing to the ever-growing list of devices.
Why is endpoint security important?

Endpoint devices have a direct connection to the corporate network. Without critical security controls in place these devices can become compromised and provide attackers with the means to further infiltrate the network. Endpoint security hardens devices against exploits as part of a multi-layered data loss prevention and cybersecurity strategy.
As with the self-driving vehicles example, devices that we would not normally consider to be endpoints are now meeting the criteria. As more devices are equipped with network connectivity endpoint security will become a relevant factor for ensuring the safety of these devices as well. Without sufficient security measures in place these devices can pose a threat to the people and organizations that use them.
Endpoint protection software and security solutions
As with any other robust cybersecurity strategy, the protection of endpoints revolves around a layered security approach that protects the devices from multiple attack vectors. To better illustrate the elements behind this, it helps to understand the types of endpoint security software and strategies that are used to secure these devices.
Device protection

This element focuses on directly protecting the device itself. The tools used to protect devices include antivirus and antimalware software as well as physical security controls to prevent devices from being lost or stolen.
Web security
A web filter improves endpoint security by protecting endpoint devices from malicious websites on the internet. These protections are achieved by either whitelisting pre-approved websites and blocking access to all other sites or through a blacklisting approach where the majority of the web is accessible with a few exceptions that are added to a blacklist (block list).
Application controls
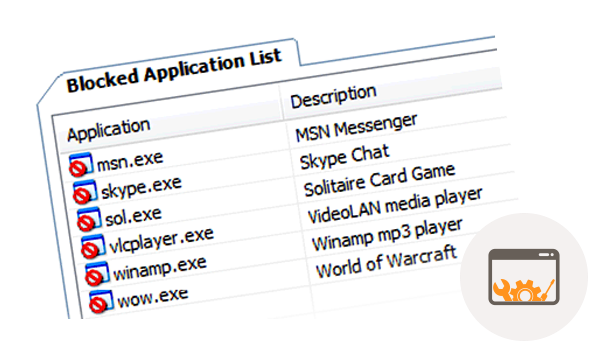
Application controls monitor and manage the level of access that applications have to endpoints as well as the access that users have to these applications. This improves the security of an endpoint by protecting it against applications with exploitable vulnerabilities. For more information about common application vulnerabilities, check out this article from Veracode.
Network security

While network security is considered a separate layer of security, the interconnectivity between endpoints and the network means that a successful endpoint security strategy includes protections for the network the devices will be connected to.
Network security is achieved through tools such as firewalls that inspect and filter incoming traffic to detect malicious data packets and network access control (NAC) tools that enforce policies that prevent users from accessing resources without authorization and meeting security compliance standards.
Data loss prevention (DLP)
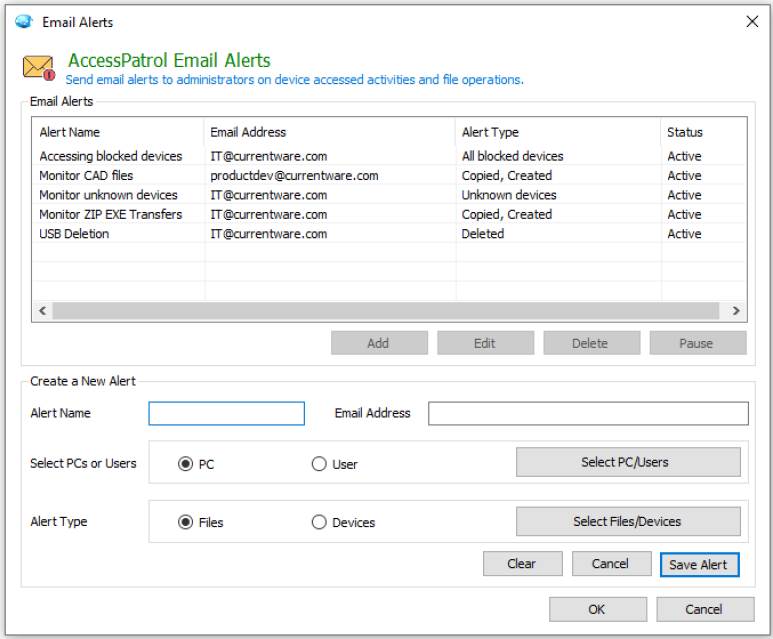
Endpoint data loss prevention solutions such as DLP software enhance security by providing controls over how data is transmitted through endpoint devices. These security tools will often include features for monitoring activities on endpoint devices to detect high-risk and unauthorized activities.
Data loss prevention can include solutions that prevent confidential information from being transmitted outside of the network and USB access control software that prevents users from connecting unauthorized USB devices to endpoints.
Administrative security

Administrative security protects endpoint devices through policies that dictate the acceptable use of technology in the workplace.
This can include:
- Data handling protocols that dictate how data must be stored, shared, and transmitted
- Acceptable use policies (AUP) that address undesirable behavior that may put endpoints at risk such as high-risk web surfing, downloading programs, and neglecting to lock down workstations when not in use.
- Policies surrounding the organization’s guidelines on use of personal devices in the workplace (Bring Your Own Device/BYOD)
- Password management expectations including how passwords are stored, complexity requirements, and best practices for keeping passwords secret.
- Cybersecurity training for employees that educates them on their security responsibilities, common exploits, and best practices for improving cybersecurity at the user level.
Free eBook:
5 Common Cybersecurity Threats in 2020
Learn cost-effective solutions to protect your business
against cybersecurity threats in 2020
Examples of endpoint protection software
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) software is used to detect more advanced threats. These tools continuously monitor endpoint devices and network activity for anomalous behavior that could be an indicator of compromise (IOC).
These tools help protect devices against:
- Fileless Malware: Malicious software that does not require the launch of an executable file to infect devices. These attacks use legitimate tools that are built into the computer’s operating system to execute the attack. This includes macros executed through Microsoft Office products as well as malicious PowerShell scripts.
- Zero-day Exploits: Vulnerabilities that have not yet been discovered and patched by the manufacturers of the product that is being exploited.
- Polymorphic Malware: Malicious software that uses machine learning (ML) and artificial intelligence (AI) to alter its code in order to evade detection from traditional signature-based antivirus and antimalware solutions
EDR tools complement prevention-based tools as part of a layered security approach. Should the threat not be detected by the first line of defense the EDR platform provides another opportunity for an attack to be mitigated. Once the EDR tool detects potentially malicious behavior it will send an alert to a designated cybersecurity expert for validation.
USB access control
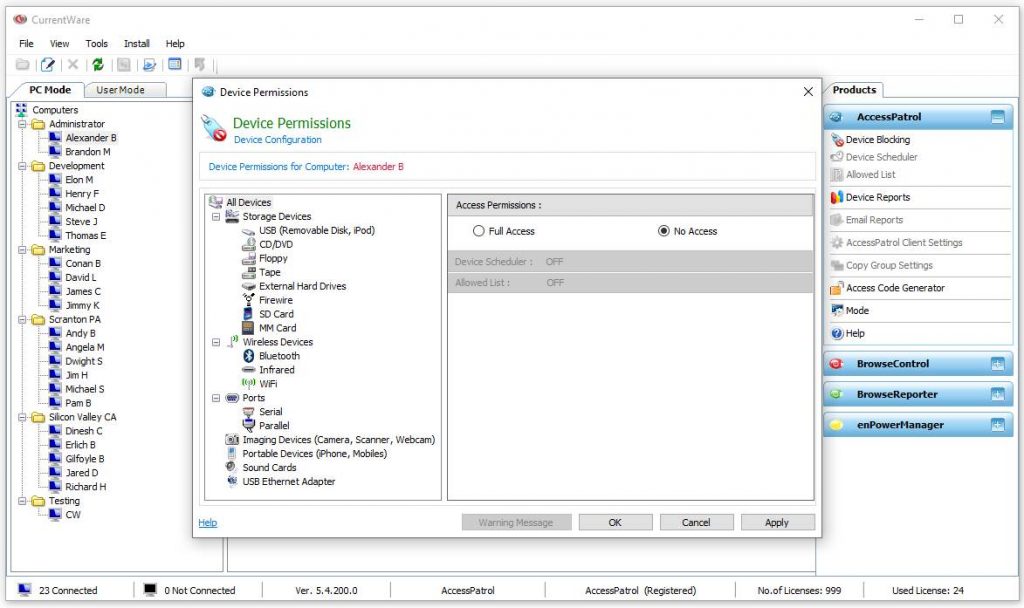
These endpoint security solutions provide software-based enforcement for USB security policies. Companies will use USB restriction software to protect endpoint devices by preventing users from connecting unauthorized USB devices.
Use cases for USB restriction:
- Prevent USB devices being used to maliciously or accidentally transmit malware
- Stop employees from using unauthorized personal devices on company devices
- Mitigate data theft through data transfer hardware such as flash drives and external hard drives
- Provide greater control over data flow in the organization by preventing employees from using USBs to bypass existing data channels
CurrentWare’s AccessPatrol is an example of USB access control software used by companies of all sizes to protect endpoints and sensitive data against peripheral devices.
In addition to disabling USB ports, AccessPatrol protects endpoints and data by:
- Monitoring endpoint activity and generating reports of device usage and file operations for review by corporate IT security personnel.
- Blocking external devices such as mobile phones, optical media, memory cards, printers, and bluetooth connections.
- Prevent illicit data transfers by blocking sensitive file types from being copied to removable media devices.
Next-generation antivirus and antimalware (NGAV)

Traditional antivirus and antimalware software secure endpoints by identifying software that is known to be malicious using signatures. As the threat landscape continues to evolve and the amount of malicious software grows exponentially these solutions evolved into what is now known as Next-Generation Antivirus (NGAV).
There is no standard definition of what qualifies as an NGAV, though there are some common traits such as added capabilities with machine learning, artificial intelligence, and data analytics technologies. Rather than focusing solely on a specific signature, NGAVs gather threat intelligence by studying the behavior of software. Patterns that indicate that the software is malicious in nature will cause the NGAV to quarantine the malware and alert administrators for investigation.
Mobile device management

Mobile devices such as laptops, tablets, smart phones, and wearables introduce added vulnerabilities due to their portability and wireless connectivity. Mobile device management (MDM) and enterprise mobility management (EMM) tools are often used to increase the security of mobile devices by providing added monitoring and management capabilities.
How MDM tools protect mobile endpoints:
- GPS Location: MDMs help locate lost or stolen devices by transmitting GPS coordinates to a dedicated console. This is particularly useful for employees that often work while travelling as they are at a higher risk of having their mobile devices stolen.
- Data Wiping: An MDM can remotely delete sensitive data to prevent a data breach caused by a lost or stolen device. They will often have the ability to delete sensitive data while leaving non-sensitive data untouched, making them valuable for companies that allow employees to use personal devices as part of a BYOD policy.
- Mobile Threat Containment: When suspicious files are detected on the mobile device, the MDM can contain them in a virtual machine to restrict the damage that they can cause to the device. Once the suspected file is determined to be safe it can then be readily accessed on the device.
Conclusion
The concept of endpoint security encompasses a wide variety of tools and procedures that are designed to protect devices that are on the outer perimeter of the network. With the widespread adoption of cloud computing and the proliferation of devices with enhanced connectivity what constitutes an endpoint is rapidly changing. The methods of endpoint security will continue to evolve alongside new technology and the growing threat landscape that accompanies them.



